How to end the headache of
inefficient privileged ID access and passwords
Establishing and managing individual IDs for each server is an unpleasant burden for corporate management. Because programs and applications require privileged IDs, passwords are difficult to change and must be shared. It’s hard to identify individuals who used those IDs. There’s your security threat. In addition, it’s extremely difficult to check the each server’s access log for the audit. Access Check is the remedy.
Improving security and efficiency while
maintaining shared privileged ID and passwords
Gateway access allows for central management of individual IDs and access logs, making it possible to enhance security without changing your typical shared privileged ID operation. Access Check creates a checkpoint to identify your employees and assess their privileges as they enter the server gateway. Central management of requests, approvals and access logs reduces the burden of matching audits and improves overall efficiency.

Controlling access and logs
is the key to internal security
Access Check works by combining the two sides of control: 1) Preventative Control, which controls access to server, and 2) Detective Control, which is log management and serves to make audits more efficient.
How the Access Check remote
desktop relay connection works
Access Check works as a gateway for a wide range protocols, such as SSH, ftp, http(s), and even RDP. After log into Access Check, users login to the target server. Access Check records all users’ input including typing and mouse operation. Access Check also tracks user operation by keeping log of recorded access.
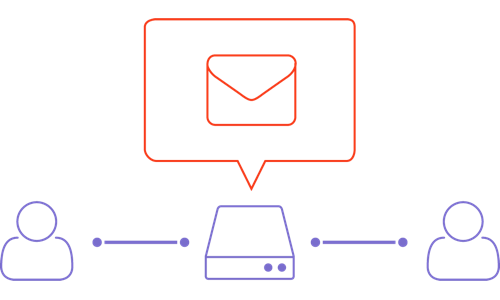
Total, centralized access control,
including access alerts
Access Check restricts user access through existing policies including user ID, network segment, protocols and more. In addition to these access controls, Access Check sends notification email to qualified personnel when user access start or end.

