Threat to people
The rate of targeted-attack email openings by executives* is 50% higher than staff members
Rate of opening targeted attack emails by executives

Analysis of our targeted-attack email simulation (targeted-attack email training) results performed in 2014 shows that about 1 in 3 (31%) executives open the emails. This rate is almost 50% higher than the likelihood of opening targeted-attack emails by staff members (19%). Our analysis also reveals that more training sessions can reduce the likelihood of opening malicious emails. To protect your organization against targeted-attacks, it is effective to regularly provide the same level of training for system-level security practices for both staff members and executives.
* In this report, “executive” refers to executive defined in corporate laws.
Threat to system
Vulnerability is exploited on the day information is made public.
Trends of detection of attacks exploiting ShellShock vulnerability (daily detection)
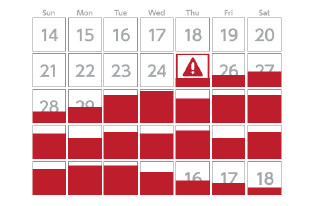
In 2014, many types of dangerous vulnerability related to products such as Bash and Struts were reported. Our Managed Security Service (MSS) detected an attack that exploited “ShellShock” vulnerability in Bash on September 25 (JST), which is the day vulnerability information is made public. Time between the moment when a product’s vulnerability is made public and the moment when an attack starts is getting shorter.
We anticipate that large-scale attacks will continue to happen in 2015, starting from the day the vulnerability is made public. It is essential to implement prompt patch management procedures and in-depth defense, such as a WAF, to secure the network infrastructure and effectively defend your organization.
System management
Companies can manage only half of their web sites.
Rate of identified websites scrutinized by the website discovery service
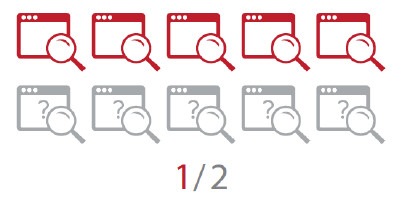
Results of our website discovery services show that only half of the websites that are identified by our discovery services are centrally managed by companies who own them. Identification of assets that require protection is an action performed before implementing security practices against vulnerability. These results show that many companies still don't sufficiently identify and manage their websites.
In addition, implementation of security practices for websites located in overseas operations is not as advanced when compared to the levels of security practices implemented in operations in Japan. To protect your organization against threats, it is critical to properly identify targets that require protection.
NRI Secure launches this integrated security service with EDR to support enterprises in the US and will deliver the service to Japan and around the world in the future.
PCI DSS
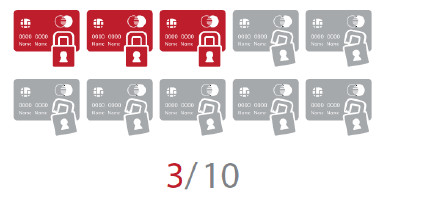
Only 30% of systems meet PCI DSS standards for external attacks.
Rate of systems that pass initial ASV scanning check
As demonstrated by the large-scale data leak by Target, an US-based company, attacks targeting credit card information are spreading all over the world. PCI DSS is an international security standard defined for protecting credit card information against card-related attacks. Analysis of our assessment data collected from our scanning services performed as a PCI DSS accredited scanning vendor, shows that only 30% of systems that received the first screening passed external vulnerability scanning.
This means that many systems that process credit card transactions have vulnerability to external attacks. In the worst case that your enterprise system is attacked and credit card information is stolen, there will be serious consequences such as business liability and declining social reputation that could affect the company's business continuity. Companies who provide credit card payments are required to review their own system’s security.










