
Author: Tomohiko Suga, IT Security Analyst
In recent years, EDR has been attracting attention as endpoint protection. EDR implementation makes it possible not only to detect and prevent endpoint threats, but also to deal with incidents that occur and investigate the events more efficiently.
It is widely recognized that EDR’s capabilities for defense, threat visualization, and incident response are necessary to acquire sufficient defense ability and interpretability against recent sophisticated attacks. Many companies are looking for a practical way to implement EDR. The following are common issues that come up under consideration:
- It is difficult to explain the security effects that can be expected from migration because the purpose and architecture are similar to installed antivirus (AV) products.
- Since the licenses of the installed antivirus products are still available, EDR needs to be operated in parallel as a migration period, but I do not know how to proceed with the migration.
This article will help explain the concept of migration, with concrete examples, while clarifying the difference between legacy AV* and EDR, to solve the challenges in migrating from AV to EDR.
* “Legacy AV” in this article refers to a product that detects malware by comparing the target file with a signature (a database packed with bytecodes and hash values of known malware). It is an antivirus solution that performs file-based detection with so-called signature matching method.
Is the Transition Necessary?
Legacy AV has been the mainstream security measure for traditional endpoints. However, since most EDR solutions are now equipped with next-generation antivirus and can improve functionality of legacy AV, more organizations have abolished legacy AV and proceeding to integrate them into EDR deployments. By unifying into EDR solutions, various benefits can be expected afterwards.
- Quality: Interrelation of antivirus functions and EDR functions is strengthened. Quality of defense and incident response is improved
- Operation: Operational resources are consolidated into a single solution, streamlining work processes related to maintenance and incident response
- Cost: License costs, operating costs, and load are reduced. TOC (Total Cost of Ownership) is reduced
Even for our clients, there are cases where response time for incidents has been shortened up to 75% by unifying them into EDR solutions. For the company where a shortage of IT human resources is particularly serious, it is important to try EDR solutions and measure the resources (man-hours) related to response when considering costs.
Comparison of Legacy AV and EDR
First, let’s sort out the differences between legacy AV and EDR.
Legacy AVs installed on endpoints operates by matching information of the target file with signatures when writing, reading, and executing a file, and determines whether the file is malware or not. Signature matching methods have the advantage that false positives (false detection of harmless software as malicious) are unlikely to occur, but on the other hand, it has the disadvantage that it can only detect attacks using known malware among all attacks using malware (file-based attacks). In other words, files without signatures (unknown malware) and attacks that do not use malware (fileless attacks) cannot be detected; it is considered difficult for legacy AV alone to respond to today’s sophisticated and complex threats.
In addition, legacy AV doesn’t have functionality to deal with threats that have bypassed detection since it is a solution specialized in threat detection. If malware that evaded detection of legacy AV infects the endpoint, it is not possible to investigate what was done by the malware or quarantine the device to prevent the spread of the infection. It will be difficult to report and explain to a third party.
Now what kind of effect can EDR have as an endpoint security measure? In general, EDR is a solution with at least the following functions. Without them, the product may not be classified as EDR.
- Detects threats on endpoints (Detection Function)
- Records (almost) all endpoint operation logs on the server in real time (Recording Function)
- Investigates the entire incident from logs (Investigation Function)
- Remotely operates the endpoint to contain incidents (Response Function)
In particular, the detection function detects threats based on all behaviors that occur on the endpoint without relying solely on signatures, which makes it possible to detect unknown malware and fileless attacks that were difficult with legacy AV. Furthermore, recording, investigation, and response functions enable response to threats that have evaded detection.
The above boils down to the conclusion that EDR is a solution that has more advanced detection and functionality such recording, investigation, and response, that legacy AV doesn’t have.
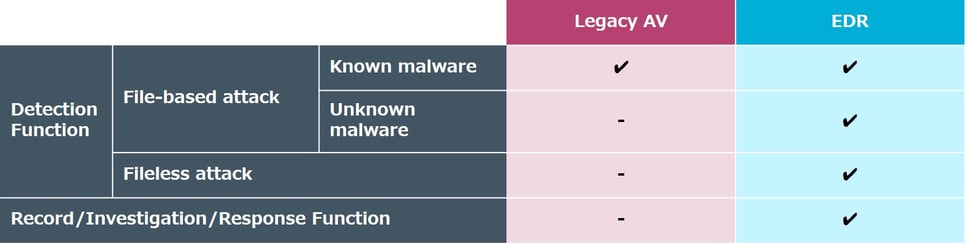
Comparison of legacy AV and EDR
It needs to be noted there are solutions that are difficult to utilize for investigation and response. (e.g. the solution only records logs related to executable files or its detection function records logs related to detected events only.)
What to Consider in Transition
Coexistence Period
In the previous section, it was explained that EDR has upward compatible performance of legacy AV and can improve the security level significantly compared to legacy AV alone. However, there are some situations where legacy AV cannot be abolished immediately for the following reasons:
- The license period of the legacy AV solution remains
- Legacy AV and EDR must coexist during verification of required EDR operations prior to implementation
- Reduction of security measures (abolition of legacy AV) takes longer due to the difficulty of obtaining an internal agreement
The problem is that it is usually not recommended operating legacy AV and EDR on a single device due to operational conflict. One example is Windows 10 automatically changes Microsoft Defender AV to passive or auto-disable mode upon installation of a third-party AV solution. (Refer: Microsoft Defender Antivirus compatibility)
Therefore, when installing EDR on a device with legacy AV, it is necessary to set the EDR detection function to temporarily degraded. The specific settings differ depending on the EDR solution, but the viewpoints that should be generally kept in mind are explained below.
The EDR detection function allows users to select the action for the detected threat from the following two operation modes:
- Detection Mode: Detect threats, but do not block
- Prevention Mode: Detect and block threats
In detection mode, when the execution of malware is detected, the malware is still running, so it is necessary to take measures such as preventing the malware from using another method. In prevention mode, malware is detected and its activity is blocked at the same time, so basically no action is required (although it is necessary to check the influence). That being said, prevention mode has a higher security level. Most of the operational conflict between legacy AV and EDR occurs when they block the same file at the same time. Here are a few points to pay attention to while configuring EDR to achieve safe operation:
- File-based Detection: Set to detection mode during coexistence because it may block the same files as legacy AV at the same time
- Fileless detection: Set to prevention mode even during coexistence because there is no possibility of blocking the same file as legacy AV at the same time
The above is a setting that considers only the operational conflicts of legacy AV and EDR. For devices that are particularly important on availability, it is also an option to set both file-based detection and fileless detection to detection mode. Detection mode cannot block threats, but it does not interfere with legitimate operations in the event of false positives, thus minimizing the impact on availability.
In addition, threat detection is effective even in detection mode. As mentioned above, EDR has recording, investigation, and response functions that legacy AV does not have, which makes it possible to greatly improve the security level of the endpoint, compared to one solely with legacy AV installed. Therefore, even during parallel operation, benefits of EDR can be fully expected by minimizing the degeneration while considering operational conflicts. However, it should be also noted that there are solutions which do not have detailed configurations of detection functionality.
Transition Procedures
Based on actual cases, we will introduce an example of transition from legacy AV to EDR. In this case, a parallel operation period of legacy AV and EDR was required for the remaining license period and operation verification.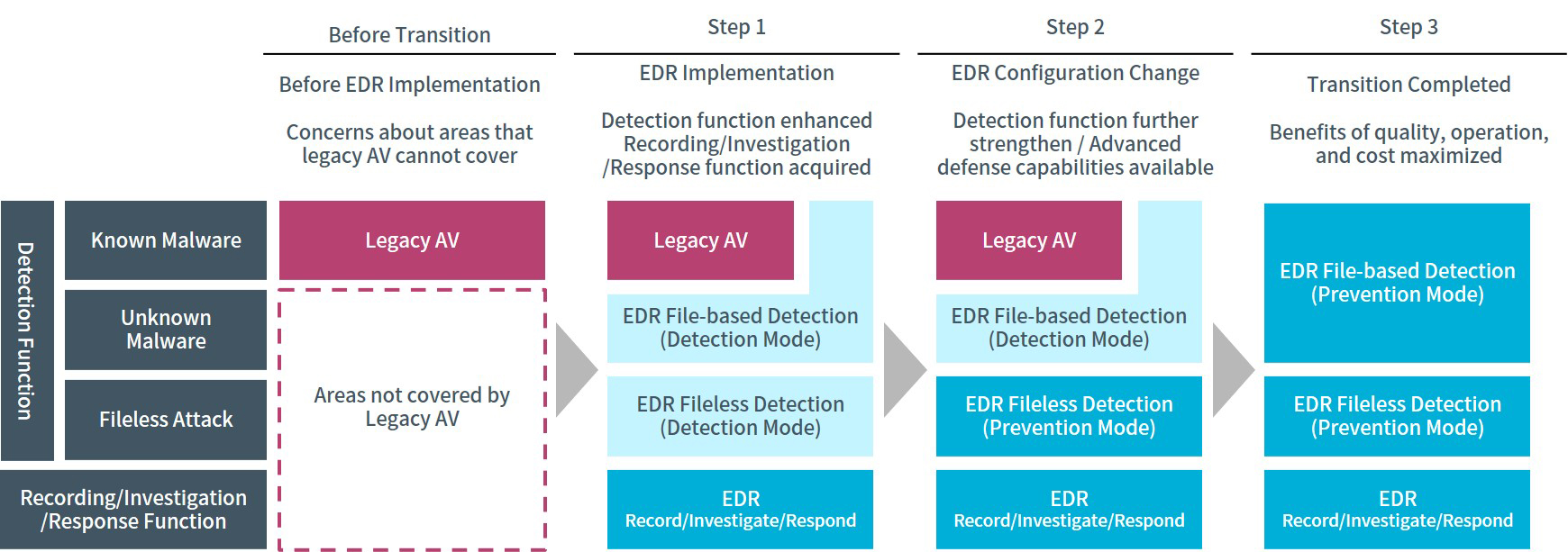

Step 1: Improve security level while suppressing business impact
In step 1, the legacy AV is not modified, EDR is introduced with the detection function set to detection mode (regardless of file-based detection / fileless detection)
The goal of this step is to verify EDR operation while minimizing the impact on availability, specifically, whether the EDR solution works as expected and whether the communication generated by log transmission doesn’t overwhelm network bandwidth.
During this step, it is normal that false positives occur at the beginning of the introduction of a new security solution, and it is essential to whitelist them (tuning); but in detection mode, though all threats targeted by the EDR detection function are detected, its operation is not blocked, so tuning can be conducting while minimizing the operational impact.
As mentioned earlier, additional capabilities of recording, investigation, and response, which enable detection of unknown malware and fileless attacks that were difficult with legacy AC, will greatly improve the security level of endpoints.
This step continues until operation verification is completed but it usually takes about one month. For systems with particularly high risk of operational impact, it is possible to leave it at this step by strengthening monitoring.
Step 2: Increase even higher defense capabilities
In step 2, the legacy AV remains unchanged and only the EDR function against fileless attacks is set to prevention mode. It is possible to significantly reduce the probability of operational impact between legacy AV and EDR, while improving the level of defense against attacks that legacy AV cannot provide.
Step 3: Complete the transition with ideal protection
In step 3, the legacy AV is uninstalled and file-based detection of EDR is changed to prevention mode. This completes the transition from legacy AV to EDR.
In this case, it took about two months to complete the transition. It is important for the security department and the systems department to share goals of risk awareness and support the execution of completing the transition early. By unifying the security measures of the endpoint into a single EDR solution, advantages in terms of quality, operation, and cost can be expected, so it is recommended to complete the transition as soon as possible.
Conclusion
In this article, we have highlighted the differences between legacy AV and EDR, and the concept of transition in order to solve the following issues that commonly occur when transitioning from legacy AV to EDR:
- Due to similar objectives and architecture, it is difficult to explain the security benefits that can be expected from transition
- It is difficult how to avoid operational impact and proceed with transition, having parallel operation of legacy AV and EDR necessary for transition
EDR has capabilities that are upward compatible with legacy AV, and we hope this article helps start consideration of transitioning from legacy AV to EDR, understanding it is possible to operate them in parallel with proper configuration.
The explanation in this article is based on the premise that the EDR platform to be introduced is an ideal solution with the performance and functions described above. The EDR market has been expanding rapidly and there are solutions that do not have the minimum functions as EDR, which have many restrictions that hinder introduction and operation in the market. If there are any doubts on selecting an EDR solution, we are here to help you, as you won’t be able to obtain the expected effect unless you select a solution that suits your purpose.
Click here for the details of our Managed EDR service.










