Nowadays, there are many incidents of information leakage due to cyber attacks and internal fraud, causing enormous damage to organizations. With the complexity of attacks and the diversification of information leakage routes, it has become difficult to prevent a wide variety of threats with measures that rely on traditional single security products. In reality, it has become important to take more realistic security measures focusing on “preventing threats” to “minimizing damage caused by threats”.
NRI Secure Enterprise Oriented SOC
NeoSOC Security Monitoring Service
NeoSOC(Security Operation Center) is a 24/7 cloud-based managed security solution that uses our SOC-as-a-Service delivery model to provide flexible service ranging from security device monitoring and alerting, to fully managed detection and response based on the individual needs of each organization.






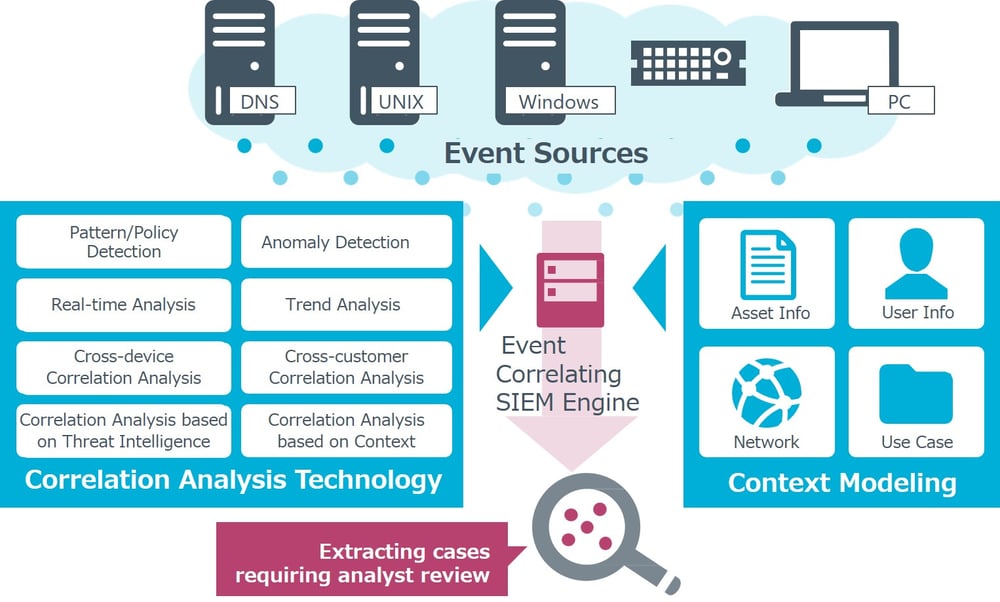
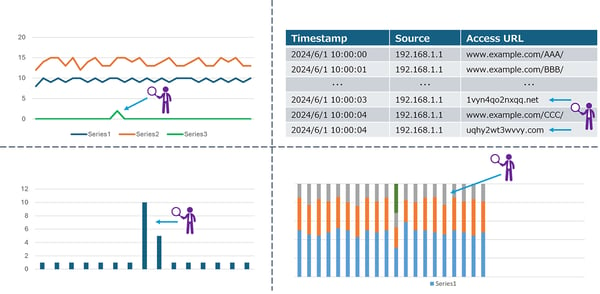
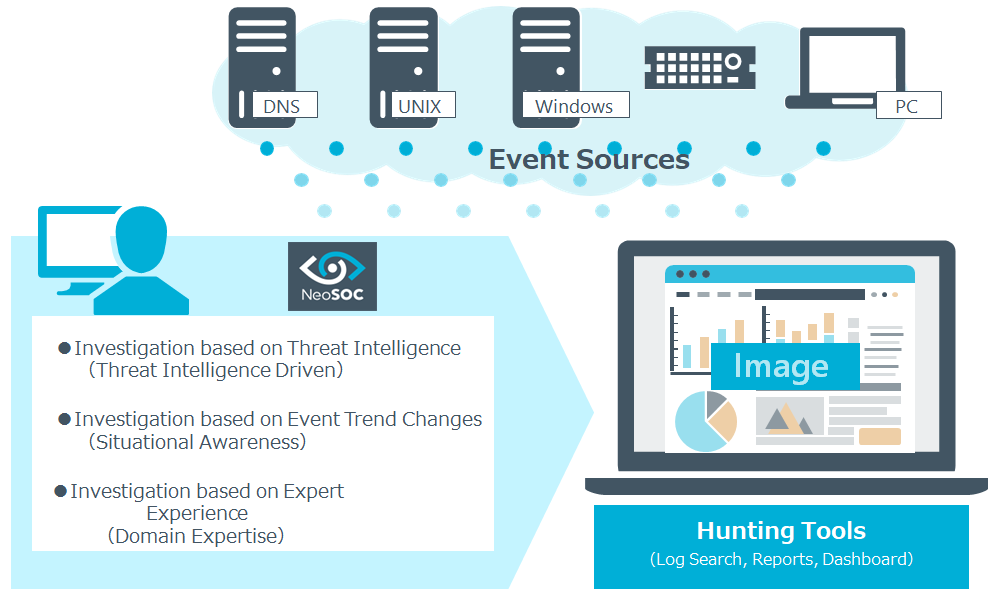
 Key Features
Key Features









