NRI Secure has been supporting various companies regardless of size or industry. Knowledge accumulated from many years of service helps present the security level that the organization should seek based on data from other companies and experience.
- HOME
- Security Consulting
- Security Policy Development Support
Information Security Policy Development Support
Overview
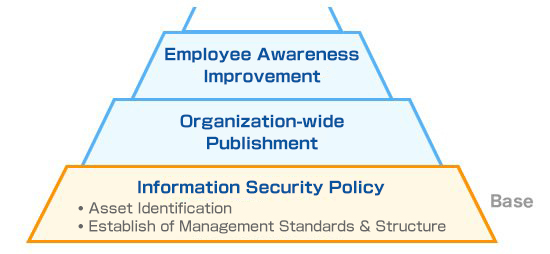
Information security policies are rules that form the basis of internal control and is important to be established considering comprehensiveness and effectiveness.
NRI Secure supports the establishment of an information security policy that suites the client’s situation, considering but not limited to: business content, information assets, systemization, and personnel organization.
Features
NRI Secure will define the assets to be protected after fully understanding the business content of customer’s organization, what kind of information assets the organization owns, and establish information security policies according to the organization’s policy and security level.
Service Description
Confirmation of Operation Flow and Information Assets
- Confirm the business/operation flow
- Clarify the information assets to be protected
- Clarify the scope of policy establishment
Confirmation of Compliance Target
- List the official frameworks and guidelines (e.g. ISO/IEC 27001, industry regulations)
- Set the framework or guideline to be used for gap analysis
Analysis of Threats and Vulnerabilities
- Understand current security controls in place
- Analyze potential risks
- Clarify threats and vulnerabilities
Information Security System Establishment
- Organize framework of applying controls in information security
Information Security Policy Establishment
- Discuss the security level that customer must meet
- Establish and effective security policy

