Triggered by ongoing measures due to the Covid-19 pandemic, a sharp increase in the number of organizations adopting remote work protocols have been observed. Initially assumed as a temporary situation, many companies are evaluating and implementing permanent policies to allow working remotely as a response to the "new normal".
Remote work allows social distancing while promoting normal functionality, but security becomes a challenge when considering its introduction and long-term operations. Concerns for system administrators are the safety and availability of confidential data that can be accessed from inside and outside the corporate network. Protection and accessibility need to be ensured at all times.
The increased utilization of cloud and communication services blur the boundaries between internal and external networks, forcing companies to assess and review their existing security architecture and policies.
One of the suitable solutions is the Zero Trust model as it has many advantages for working remotely from a security standpoint. Zero Trust is a leading model and strategy which we believe is adaptable for an environment designed where being remote is the "new normal".
What is Zero Trust?
Zero Trust is a model which devices, users, and networks are continually verified. Access to internal components, such as data and systems, are controlled based on verification.
Zero Trust was introduced by John Kindervag, a former Forrester Researcher, in 2010. A traditional model depended on a perimeter defense, which protected internal systems by defining boundaries and utilized security appliances to protect those boundaries. Zero Trust does not define boundaries, but instead uses the concept of "Never Trust and Confirm" to continually verify access. In this way, each instance in which data or network assets are requested, system and user access are certified along each step.
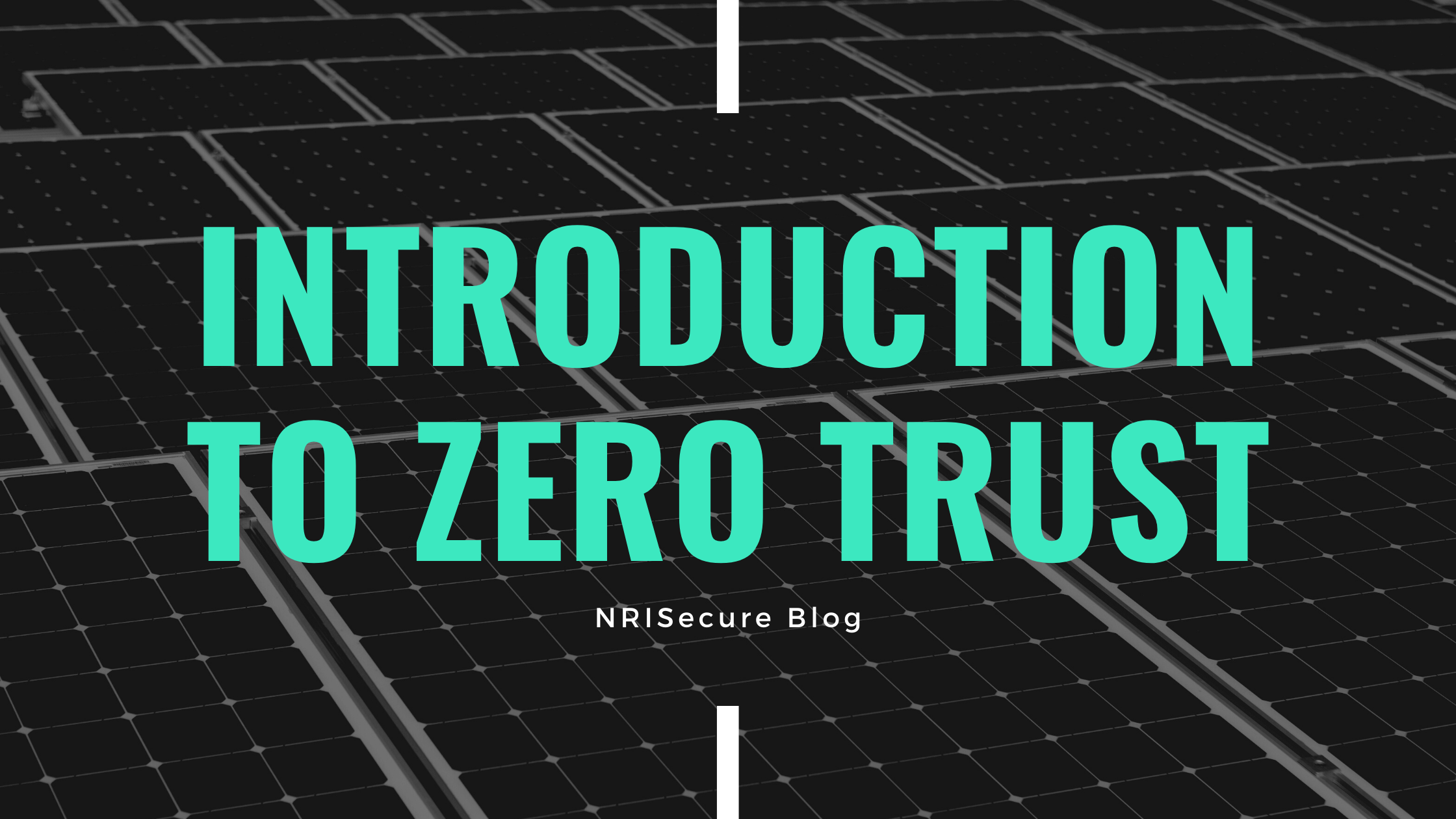
Forrester Research improved the model in 2018 with ZTX, Zero Trust eXtended. It defines seven requirements as the foundational building blocks of Zero Trust.
Zero Trust Requirements
Remote environments often pair well with Zero Trust models since it allows for multiple combinations to meet specific operational requirements, providing optimal security for each session.
Benefits of Zero Trust in Remote Environments
When applying Zero Trust to an organization, Zero Trust Extended serves as the basis for requirements. Several examples of solutions and benefits for the security of devices and networks provided by ZTX are particularly useful for working remote.
Benefit 1: Improving Network Security
Two types of connections that needs to be monitored and controlled are connections to the open Internet and connections to internal networks, as described in the table below.
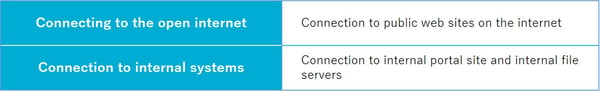 In a traditional remote environment, VPN gateways are utilized at internal and external boundaries. Users working remotely will connect to the VPN gateway for access to the corporate LAN and internal services. Zero Trust instead do not utilize VPN gateways. This section introduces an example of how Zero Trust secures open Internet connections and internal systems.
In a traditional remote environment, VPN gateways are utilized at internal and external boundaries. Users working remotely will connect to the VPN gateway for access to the corporate LAN and internal services. Zero Trust instead do not utilize VPN gateways. This section introduces an example of how Zero Trust secures open Internet connections and internal systems.
Implementation Example (1-1). Security and Protection of Open Internet Communications
First, let's understand typical security measures for open internet connections. When remotely accessed via a VPN gateway based on boundary protection, the connection is established by the VPN gateway to the corporate LAN over the open Internet. The VPN gateway allows security measures utilized inside and outside the company, such as URL filtering, virus checking, encryption, and data loss protection (DLP), to still be functional.
Limitations of VPN gateways are dictated by the available bandwidth. The more users and services that utilize the VPN gateway, the larger the bottleneck. One solution to allow full throughput while maintaining the same level of security of internal connections is the Secure Web Gateway (SWG). Secure Web Gateways allow security measures to be moved from perimeter gateways to the cloud for comprehensive web traffic protection. Since SWGs work like proxies deployed in the cloud, any open internet user can take advantage of security features regardless of device location.
Implementation Example (1-2). Security Measures for Communication to Internal Systems
Shown here is the connection from outside to internal systems. In addition to limited network bandwidth, there are other significant issues with using perimeter protection when routing VPN gateway traffic to internal and external boundaries.
One major issue is keeping ports open for remote access, exposing the connection to external attackers. In fact, many VPN gateway vulnerabilities have been reported, with even more cases of exploitation.
To address this concern, Zero Trust Network Access (ZTNA) can be utilized. The connection source is not directly connected to internal services, but through an intermediary system hosted in the cloud, etc. This allows the internal system to not require an always-on connection to the Internet, reducing risk and possibility of attack. It also optimizes communication paths for efficient and secure connections to internal systems.
Benefit 2: Improving Device Security
The Zero Trust model verifies that source devices connecting to internal systems are secure, and continually controls access to each piece of data or internal system accessed. This applies to devices configured and provided by the company, as well as personal devices utilized for work, a concept known as "Bring Your Own Device" (BYOD). Zero Trust allows security to be maintained with BYOD.
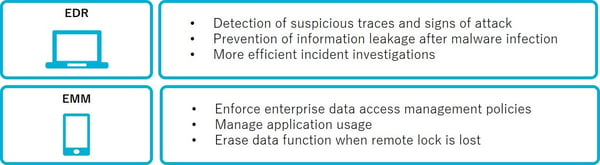
Zero Trust leverages EDR (Endpoint Detection and Response) and EMM (Enterprise Mobility Management) to improve device security by checking device status, collecting logs, and applying security compliance policies.
Example of Implementation (2-1). Checking Device Status and Managing Logs
With working remotely, it is difficult to fully understand the environment in which the user of each device resides. As a result, there is risk that a single device within the user's network may be compromised and eventually propagate to the internal corporate infrastructure.
If such a case occurs in the boundary protection model, where the state of the device is monitored and logs are collected only while it is connected to the internal LAN, it is not possible to determine when the device was compromised. That causes a delay in incident response, adds difficulty in finding the cause, and development of preventive measures.
A solution to this challenge is Endpoint Detection and Response (EDR). Taking account the increasing diversity of attack mechanisms, as well as the difficulty in preventing incidents, EDR allows enhanced response after an incident occurs. With EDR, it is possible to effectively prevent information leaks post infection, prevent further spread, and conduct investigations pertaining to the incident.
Implementation Example (2-2). Remote Management and Policy Enforcement for Mobile
Many companies use mobile devices, such as smartphones and tablets, due to multiple advantages with workflow, like communication. With many various applications and accessible content, risk of information leaks increase if security measures, based on the boundary protection model, are only applied when connected to the corporate LAN.
Enterprise Mobility Management (EMM) allows for remote management of mobile devices, ensuring consistency with security compliance policies, and application management. Remote management enables the deletion or initialization of business-critical data in the event of a loss or stolen device.
In addition, EMM also grants the ability to enforce security policies , such as but not limited to, enabling PIN upon startup, restricting dangerous modifications to the OS like Jailbreaking or rooting, etc. Application management allows advance control over application operations, from downloading apps to copy/pasting within applications, etc.
Conclusion
With working remotely being commonplace, it is necessary to shift the way of thinking from traditional assumptions when considering security measures. In the boundary protection model, ensuring security also restricted freedom in the ability to work. Zero Trust allows more flexible working styles while granting elevated security.
In this article, we introduced the benefits of applying Zero Trust from a remote perspective, but optimal implementation varies from company to company. NRI Secure offers a wide range of services to help achieve Zero Trust, from overall design, to solution implementation and operation.










