
Author: Kiyoshi Akuta, IT Security Analyst
Among consultations regarding security incidents caused by malware infection, there are certain number of cases caused by “unmanaged device(s)”. In these incidents, devices that were not properly managed as corporate assets, referred to as “stray devices”, were infected with malware and spread to other devices within the network. Based on the cases so far, there is a strong tendency that it occurs at regional and overseas bases where asset management is a challenge.
Stray devices are devices that cannot be forced to implement security measures by mechanisms, such as Active Directory, and tend to be the starting point for malware infection. In addition, it is often difficult for the administrator to know of the infection and the scale of damage, as it tends to increase as the detection is delayed.
Under these circumstances, many administrators are being forced to take measures in addressing major issues of asset management, detection of, and response to cyberattacks. It has become a large concern for many organizations.
What can be done to achieve those goals at once? Introducing a new approach of security measures including asset management at the endpoint.
1. Difficulties of Asset Management
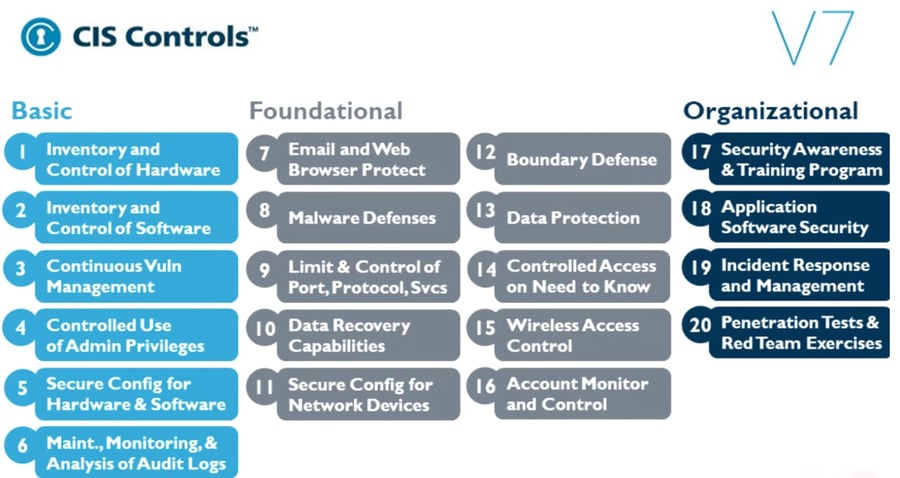
As mentioned above, asset management has the important meaning of eliminating unknown devices and enabling security control. CIS Controls, developed by the US Center for Internet Security (CIS) in collaboration with the National Security Agency (NSA) and the National Institute of Standards and Technology (NIST), states “Inventory and Control of Hardware” and “Inventory and Control of Software” as high-priority basic items.
On the other hand, items such as “Malware Defenses” are listed as foundational, and it is described that it is an appropriate approach to maintain after basic items are implemented.
In reality, there are many companies that cannot proceed with maintenance in such a straightforward manner. One of the many factors is the sophistication of cyberattacks. According to a survey by cybersecurity firm CrowdStrike, more than half of the attacks observed in recent years are attacks that are difficult for traditional antivirus solutions to detect, and it is not possible to expect 100% protection by antivirus alone. In order to respond to sophisticated attacks, the priority of introducing a mechanism to detect and respond to attacks, such as Endpoint Detection and Response (EDR), is high.
Another factor is the lack of human resources for security measures. In a survey conducted by NRI Secure in 2019, about 90% of companies answered that there was a shortage of personnel engaged in security measures, and it shows the ability to propel security measures forward is insufficient.
With the sophistication of cyberattacks and the shortage of security personnel, it is not possible to promote the development of measures in the order of “asset management” to “protection, detection and response” with urgency. There is no choice but to prioritize counter measures against cyberattacks that are currently occurring. From now on, it is expected that an approach will be further required, which can easily improve asset management while responding to cyberattacks.
2. Utilizing Endpoint Detection and Response (EDR) for Asset Management
How can it be achieved? One option is to utilize an additional feature of EDR.
It is common to use “dedicated” asset management solutions for asset management, but recently EDR has introduced products equipped with an asset management feature. In addition to the original purpose of EDR, “detection and response to cyberattacks,” we will introduce the advantages of using asset management features.
2-1. Easy Grasp of Managed Asset Information
There are two main types of asset management solutions, depending on whether or not a program called an agent that runs on the endpoint is required. The following is a brief summary of each method.
|
Method |
Overview |
Pros |
Cons |
|
Agent |
An agent is installed on each device and collects asset information. |
- A lot of information can be collected - It works offline and can be collected when it comes online |
- High installation load (agent installation required) - The management of agent software is necessary |
|
Scanning |
Access each device from the management server and collect asset information. |
- Low installation load (no work required at each endpoint for installation) - No need to manage agent software |
- Device and network bandwidth load occur when exploration is executed - The device must be online when scanning - The amount of collected information may be small if administrator privileges are not available |
From the viewpoint of the information that can be collected, many of the products in circulation use the agent type. Many EDRs are agent based and by using the asset management feature, it is possible to eliminate the need for installing agents for the purpose of asset management only. Asset management can be started quickly with a low load. In addition, since it operates with a single agent, the required machine resources can be reduced, the effect of reducing the impact on the business can be expected.
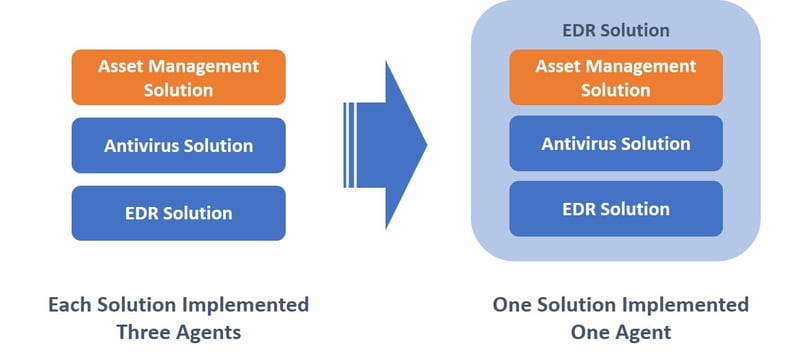
2-2. Easy Discover of “Stray Device(s)”
Another advantage is that you can easily know whether or not EDR has been implemented to the endpoint.
With the asset management features of EDR, it is possible to detect devices that do not have EDR installed on the same network. Using this feature, the load of searching for stray devices can be expected to be reduced.
If there is a device that does not have EDR installed and receives a cyberattack, the attack cannot be detected and may be compromised. Attackers who infringe upon devices in an organization tend to use devices that have not been installed with security products as a hiding place and spread the infringement further, so it is important how to find stray devices and put them under control.
3. Conclusion
If you focus only on “asset management”, it’ true that the solution dedicated to asset management is functionally superior; on the other hand, the benefits of implementing EDR and asset management as part of a single solution is likely to be sufficient.
For those who are looking for quick and easy asset management, or who are considering its implementation, why not consider using the asset management features of EDR as an option?
In general, EDR often has the feature set of collecting detailed information of and controlling the device. Technically, it can be applied to many scenarios. An increasing number of products have multiple functions such as USB control, vulnerability, and firewall management. In the future, it is expected that a single solution will reduce load and cost without having to worry about a wide variety of products and discrete operations.
Related service: Endpoint Monitoring










