
Author: Jun Yano,
Information Security Consultant (CISSP, CISA)
From late 2022 to early 2023, Australia experienced a surge in cybersecurity incidents, with news about these crimes becoming viral in the media daily.
During this period, I had the opportunity to work in Sydney, Australia, as a trainee from October 2022 to September 2023. This allowed me to witness firsthand how these incidents impacted Australian businesses and society. In this article, I share insights into the cybersecurity landscape in Australia during this time.
Massive Data Breach on Optus
In September 2022, a hacker named "optusdata" claimed to possess 9.7 million customer records of Optus, the second-largest telecommunications company in Australia. The hacker demanded 1.5 million Australian dollars(A$) within a week, threatening to sell the information if the ransom was not paid. The compromised data included 2.1 million customer ID numbers, of which 1.2 million were still valid at the time of breach. The hacker revealed that they exploited an insufficiently managed API exposed to the internet at the interview by the news reporter. After the first threatening message, they posted 10,000 customer records on a hacker forum as a warning to Optus.
In response, "Operation Guardian" was launched by Australian Federal Police and state and territory police, collaborating with financial institutions to protect victims from cybercrimes such as identity fraud. They reinforce the monitoring for abuses of victims’ personal information. After the launch of this project, A 19-year-old in Sydney was arrested for blackmailing victims, demanding A$2,000, and sentenced an 18-month Community Correction Order (CCO) and 100 hours of community service. A little later, "optusdata" suddenly withdrew the ransom demand and posted the message of apology for victims whose personal information was exposed, and promised to delete whole stolen information. Assistant Treasurer Stephen Jones implied that this ransom was more likely to be conducted by a kid in garage, not a state-level actors considering their immature behaviors. Optus estimated the data breach would cost at least 140 million A$, facing class actions from affected users.
Disruptive Data Breach on Medibank
Simultaneously, Medibank, one of the largest health insurance companies, faced a cyber security incident. In October 2022, 200GB of data containing 9.7 million customer records, including sensitive medical history records, was stolen. Medibank detected unusual activities, prompting the immediate shutdown of some systems. I remember that TV news reported this panic arose by sudden system down. Several days after, Medibank confirmed the leakage of their customer information and received the request for 15 million A$ ransom from hackers. Medibank had kept refusing to pay ransom in line with the instructions from the government and cybercrime experts. They advised that there was only a limited chance paying a ransom would ensure the return of our customers’ data and prevent it from being published. After refusing to hacker’s requests several times, they published a segment of the stolen customer information on the dark web. This divulged sensitive information contained medical history records of customers who have undergone treatment for mental health such as dementia, heart disease and abortions etc.
In November, Australian Federal Police decided to expand the scope of “Operation Guardian” to cover the victims of Medibank’s data breach and mentioned “This is important because we believe that those responsible for the breach are in Russia” and “What I will say is that we will be holding talks with Russian law enforcement about these individuals”. After Medibank continued refusing to pay ransom several times, finally this hacker posted all stolen information on the dark web and terminated the negotiation by announcing “case closed”.
The method used in this incident is considered as one of the “Supply Chain Attacks”. As the first step, hackers obtained credentials which was initially provided to a contractor of Medibank and it allowed them to infiltrate the Medibank systems. After the initial intrusion, they repeated stealing other credentials inside the systems and went deeper and deeper into the system and finally accessed customer information.
In 2022, Medibank reported a loss of 46.4 million A$, with an expected loss of 30 to 35 million A$ in 2024.
Government’s Responses to Multiple High-Profile Data Breaches
Beyond these two incidents, other companies, such as Telstra, Dialog, and Mydeal, also suffered cyber security incidents. In response, Minister for Home Affairs and Cyber Security, Ms. Clare O’Neil, emphasized the need to strengthen government powers during emergencies and share crucial information with financial institutions promptly.
In December 2022, "The Privacy Legislation Amendment (Enforcement and Other Measures) Bill 2022" came into effect, enabling fines for organizations causing serious or repeated cyber security incidents. The fine could be the greater of 50 million A$ or three times the value of any benefit directly or indirectly attributable to the conduct constituting the breach or, if the court is unable to determine the value of that benefit, 30 per cent of the adjusted turnover of the company during the turnover period of the contravention (This fine used to be a maximum of 2.2 million A$ before this amendment).This amendment also empower the government to reach the necessary information in a timely manner and enables them to share information with financial institutions in order to prevent further financial damage for citizens from the incidents.
Additionally, government established “National Office for Cyber Security” under the Ministry of Home Affairs in March 2023 and announced a plan to create 7-year cyber security strategy until 2030. Ms. O’neil stated that this strategy is to make Australia “the most cyber secure country in the world by 2030” and implied that it enables the “Hack back” operation against threat actors. Ms. O’neil has kept discussing with stake holders and cyber security experts and in September 2023, Mr. Darren Goldie assumed National Cyber Security Coordinator.

Cyber Security Maturity Level of Australia
Following the consecutive incidents from late 2022 to early 2023, more cyber security breaches occurred, including the data breach of 14 million customer records from Latitude Financial and information leakage from HWL Ebsworth, impacting over 60 organizations, including government agencies and major corporations.
In the case of Latitude Financial, the retention of unnecessary personal information exacerbated the incident, resulting in a loss of 76 million A$ in early 2023. In the case of HWL Ebsworth, this massive data leakage involved major enterprises and government agencies such as Australian Federal Police and The Office of the Australian Information Commissioner(OAIC)※1 which had worked on other cyber security incidents introduced in this article.
In Australia, Australian Signal Directorate(ASD)※2 established Australian Cyber Security Centre(ACSC)※3 and they published Essential Eight※4 which is the eight principles for cyber security and ACSC and AustCyber※5 promote the cyber security for organizations in Australia.
In addition, ASD launched REDSPICE※6 which is the cyber security enhancement program. However, during my 1-year stay in Australia, I saw many Australian companies are still working on the ISO 27001 certification. It seems to me that the progresses of cyber security in Australian companies are a bit behind compared to companies in Japan.
This is not a comparison between Australia and Japan, but Ms. O’neil mentioned at the interview by ABC, “I just want to note that we are probably a decade behind in privacy protections where we ought to be. I would say we're about five years behind in cyber protections than where we should be given how fast things are moving”.
This is a bit different perspective from the cyber security initiatives, but AustCyber released ”Australia’s Cyber Security Sector Competitiveness Plan 2022※7” and this report indicated that annual revenue growth of cyber sector in Australia is slower than other leading nations.
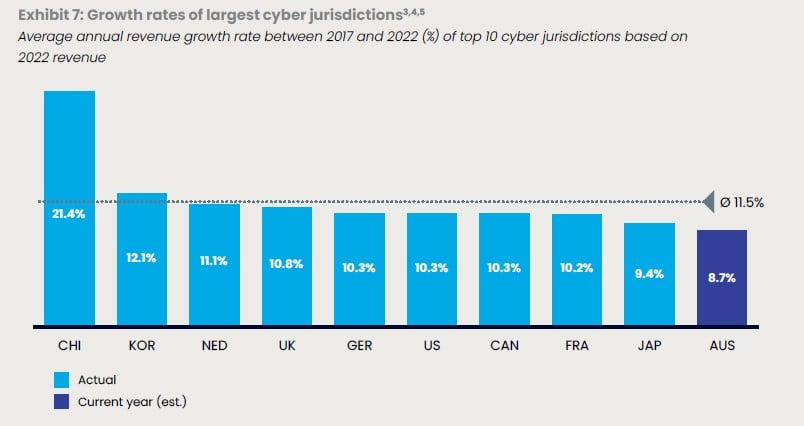
Excerpt from Australia’s Cyber Security Sector Competitiveness Plan 2022
https://www.austcyber.com/resource/australias-cyber-security-sector-competitiveness-plan-2022
According to ”Notifiable Data Breaches Report: July to December 2022※8” published by OAIC, the number of information leakage by ”Malicious or Criminal Attack” has increased by 41%(From 249 cases to 350 cases) in late 2022 compared to early 2022. The number of information leakage over 5,000 has increased from 24 to 40 as well. This could be considered that these trends are attributed to the insufficient cyber security protection in Australia.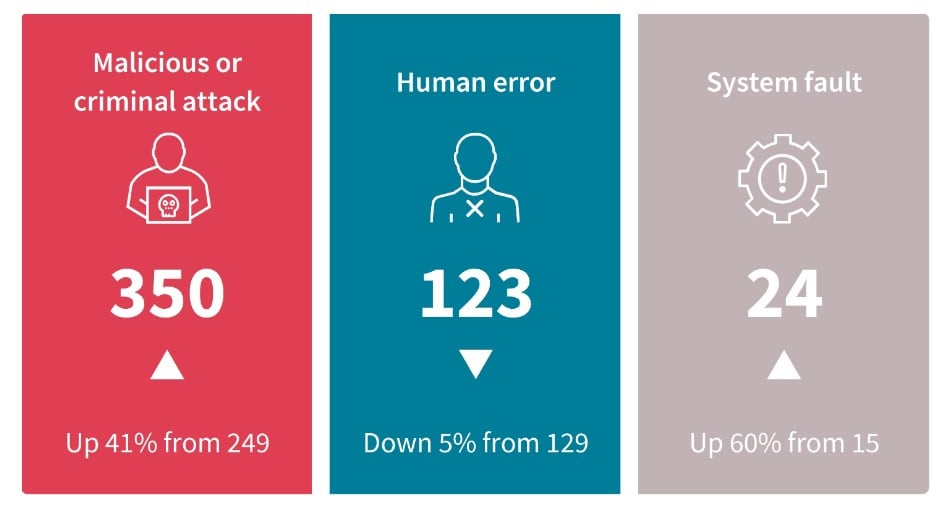
Excerpt from Notifiable Data Breaches Report: July to December 2022
While this trend seemed to be a major change, it could be a temporary increase of cyber attacks because it turned out that these numbers decreased again in the following period, early 2023. But not a few people wondered why so many devastating data breaches happened to Australia during this period. According to “ASD Cyber Threat Report 2022–2023※9” published by ASD on November 14th 2023, a series of cyber attacks from late 2022 to early 2023 can be divided into “opportunistic attack” and “more deliberate attack” and most of surges from previous period are dominated by “opportunistic attack”. This fact indicates that not only impulsive cybercrimes by young kids, but also deliberate attack from state-level threat actors hit Australia simultaneously during this period.
This report also pointed out Russia’s Federal Security Service’s cyber espionage activities with using the malware called “Snake” and attacks on the critical infrastructure organizations by state-level actors in China.
After all, most of those attacks during this period were considered as “opportunistic attack”. But overlapping of different type of threat actors might have contributed to this surge of cyber security incidents.
※1 The Office of the Australian Information Commissioner
https://www.oaic.gov.au/about-the-OAIC
※2 Australian Signal Directorate(ASD)
※3 Australian Cyber Security Centre(ACSC)
https://www.cyber.gov.au/about-us
※4 Essential Eight
https://www.cyber.gov.au/resources-business-and-government/essential-cyber-security/essential-eight
※5 AustCyber
https://www.austcyber.com/about-us
※6 REDSPICE
https://www.asd.gov.au/about/what-we-do/redspice
※7 Australia’s Cyber Security Sector Competitiveness Plan 2022
https://www.austcyber.com/resource/australias-cyber-security-sector-competitiveness-plan-2022
※8 Notifiable Data Breaches Report: July to December 2022
※9 ASD Cyber Threat Report 2022–2023
https://www.cyber.gov.au/sites/default/files/2023-11/asd-cyber-threat-report-2023.pdf
Public Release of 2023-2030 Australian Cyber Security Strategy
“2023-2030 Australian Cyber Security Strategy※10” released on November 22nd, defined six cyber shields with the aim of protecting Australian citizens and businesses. The strategy outlined three phases (Horizon1, 2023-2025; Horizon2, 2026-2028; Horizon3, 2029-2030) and detailed initiatives for each phase. The accompanying "2023–2030 Australian Cyber Security Strategy ACTION PLAN" provided specifics on initiatives and accountable agencies for Horizon 1. The Australian government announced that they decided to allocate an additional 586 million A$ to the 2.3 billion A$ already allocated for cyber security.
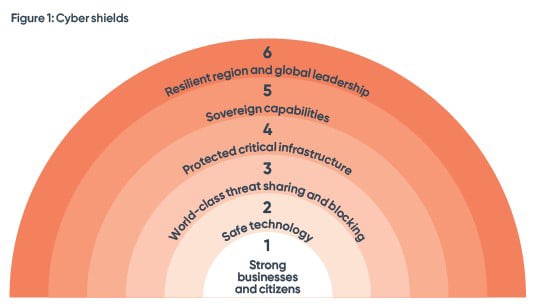

※10 2023–2030 Australian Cyber Security Strategy
https://www.homeaffairs.gov.au/cyber-security-subsite/files/2023-cyber-security-strategy.pdf
※11 2023–2030 Australian Cyber Security Strategy ACTION PLAN
Differences in Responses between Australia and Japan
When it comes to responses for serious cyber attacks, Japan had similar situations in the past such as a series of SQL Injection attack against e-Commerce web sites, worldwide cyber attacks against Japanese organizations by a hacktivist group “Anonymous”, and sophisticated phishing attack on Japan Pension Service etc.
However, it seems to me, that there is an obvious difference in the response between Australia and Japan. In the case of Japan, every organization responded quickly and keep certain level of cyber security even after several years. But I haven’t heard that any organization in Japan, including the government, set an ambitious goal and made a long-term strategy for cyber security.
In the case of Australia, Minister for Cyber Security spearheaded the incident response project, not only resolving incidents but also establishing a comprehensive cyber security strategy for 2030. It looks that they took advantage of the negative events to create the positive future growth of their nation. This is my opinion, but difference in approach appeared rooted in national characteristics, such as leadership and followership, rewards and discipline. This is not about which is the better, but it seems as a very insightful difference to me.
As I mentioned, while I have an impression that Japan is slightly advanced against Australia in terms of cyber security maturity at this moment, the proactive steps taken and ambitious goals set by Australia suggest an exciting trajectory. I definitely say it is worth keeping your eye on how Australia evolves along with their strategy and see if they would be “the most cyber secure country” by 2030.










