
While remote work has been vastly expanded under the influence of the COVID-19 pandemic, there are many cases in which business activities have been brought to a halt due to ransomware attacks. In IPA’s “10 Major Security Treats 2021”, “Ransomware damage” jumped from 5th to 1st in terms of threats from an organizational perspective.
Damage to large companies are conspicuous, but as the Ministry of Economy, Trade and Industry warns, small and medium-sized companies are also suffering. We should consider that any company can be targeted.
Ransomware is a type of malware. While the scope of damage from general malware is limited, ransomware damage is apt to cause an outage for most businesses and services over a wide area of the corporate network. Therefore, it is recommended to consider ransomware attacks as an issue of business continuity and it is necessary to improve the ability to identify, defend, detect, respond to, and recover from the threat of ransomware attacks. It is also important to continuously improve and conduct training based on a business continuity plan.
Checklist to Prepare against Ransomware Attacks:
- 1) Is there a plan to communication internally and externally after the incident?
- 2) Is it confirmed that data can be restored with backups?
- 3) Who is in charge of negotiation with the attacker?
- 4) Who can direct the incident response?
- 5) Are risk funding and cyber insurance prepared?
- 6) Is the entrance point of remote access secured?
- 7) Are you prepared for email threats?
- 8) Is the authentication system secure?
- 9) Is network segmentation and traffic control appropriate?
- 10) Is sufficient threat detection capability implemented?
- 11) Can you contain threats?
- 12) Can you identify the signs of an attack?
- 13) Are you trained and tested against attacks?
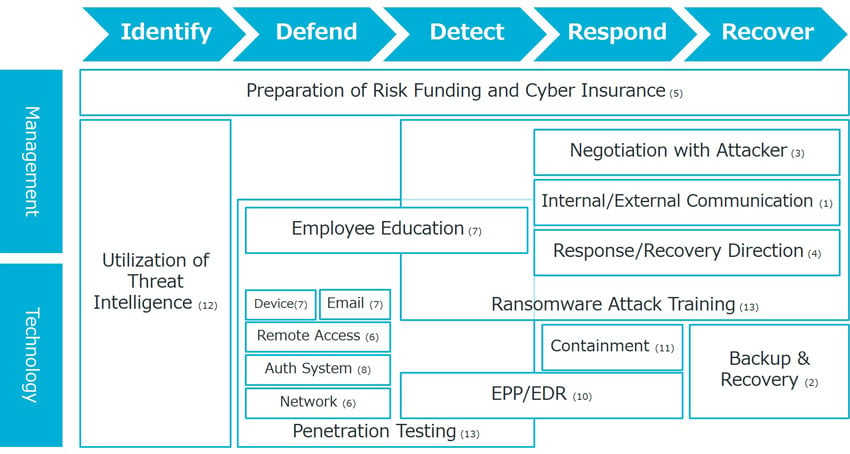 Figure: Overview of Preparation against Ransomware Attack
Figure: Overview of Preparation against Ransomware Attack
If you find it difficult to give a clear answer to these questions, consider “preparing” for a ransomware attack using the following as tips:
1) Is there a plan to communication internally and externally after the incident occurs?
Attackers target a wide range of corporate networks all at once, interrupting employees’ access to data and disrupting business.
Under such circumstances, it is important for management to decide what to notify or what to not notify for employees, risk management office, customers, and related external organizations.
It may also be useful to have connections with an outside expert who can communicate appropriately in these situations.
2) Is it confirmed that data can be restored with backups?
Once attacked, the attacker often demands a high ransom instead of providing the key to recover the encrypted data. The decision on how to deal with the demands would be different depending on whether data is restored from backup and confirmed that it can be restored for business continuity within an acceptable time.
Even if it can be confirmed that restoration by disaster recovery is possible, it is not enough. Applications used for data recovery as well as any backup datasets may be unavailable due to encryption from the ransomware attack. It is important to make sure that they are protected from being encrypted by ransomware.
Some may think, “We will pay the ransom and decrypt the data, so we don’t need to check if we can restore or not”. It is not guaranteed that the data can always be restored. Worst case scenario, it should assumed that data cannot be fully restored even if the ransom is paid.
3) Who is in charge of negotiation with the attacker?
So, if you can restore quickly, you don’t have to pay the ransom? Unfortunately, that is not the case. Even if you can say “we will not pay the ransom because we can restore the data ourselves”, the attacker may threaten with "If you don’t want us to disclose the stolen data, pay the ransom”. You should expect to negotiate with the attacker, whether or not the restoration capability is perfect.
It is a good idea to consider contracting a professional negotiator in advance to reduce the ransom and save time since the attackers are considered ransomware professionals. Once the aforementioned preparations are in place, let’s reduce the risk of being attacked.
4) Who can direct the incident response?
While preparing an external communicator, it is also necessary to have a system in place to promote incident response practices within the organization. Generally, a Computer Security Incident Response Team (CSIRT) is responsible for that. If you have systematic concerns about responding to ransomware attacks, it is better to select a service that can get the cooperation of external experts such as “security incident response support” and immediate cooperation in case of an incident.
5) Are risk funding and cyber insurance prepared?
If you become the victim of a ransomware attack, the cost of responding will not be low regardless if the ransom is paid. It is expected that the reputation damage will affect profits or increase the cost of campaigns to repair it. Estimate how much it will cost for response and record it in the risk fund. If the cost exceeds what is affordable, consider subscribing to cyber insurance.
6) Is the entrance point of remote access secured?
So far, we have prepared for response after being attacked. From here, we will strengthen the defense to reduce risk of being attacked.
Why did ransomware attacks increase during the COVID-19 pandemic? More and more companies are utilizing virtual private networks (VPNs) and remote desktop connections (RDPs) to connect their employees from their homes to corporate networks. Since VPNs and RDPs always face the internet, vulnerabilities in corporate networks can be exploited by attackers to break into the environment. It is necessary to make sure that there is no vulnerability at the entrance of remote access that allows unauthorized intrusion from a remote location. It may be a good idea to use a service like “platform assessment” to identify vulnerabilities quickly and reliably.
7) Are you prepared for email threats?
Attackers attempt to intrude not only through remote access points, but also through emails. Threat-based email protection solutions can help combat email intrusions. We provide Proofpoint Software-as-a-Service (SaaS) as a targeted email attack and business email fraud (BEC) solution.
Still, some threatening emails can slip through and reach an employee’s inbox. In such a case, it is recommended to educate employees not to act carelessly, create an environment that is easy to report the email, and receive or repeat training. It would be a good idea to consider a solution or service such as “phishing awareness training / phishing simulation tool” by Cofense.
Also, in the unlikely event that such an email leads an employee to a malicious website, updated software on the device can reduce the possibility that malware becomes the starting point of an attack and lead to larger vulnerabilities.
8) Is the authentication system secure?
An attacker who breaks into a corporate network may attempt to hijack an authentication system. For example, a vulnerability called ZeroLogon could be exploited to gain domain administrator privileges from Windows Active Directory and allow the attacker to act freely within the domain.
In the medium-to-long term, it is recommended to consider moving to a network that allows users access to the corporate network only after authentication. Migrating the authentication system to Identity-as-a-Service (IDaaS) enables users to log in from anywhere. Furthermore consider adopting Zero Trust Network Access (ZTNA) services that works with IDaaS.
By doing so, VPNs will no longer be necessary and you will be freed from worrying about being intruded via VPN. RDP services will not be kept open to the internet, so you don’t have to worry about intrusion via RDP as well. It is advisable to plan a shift from so-called perimeter defense security to zero trust security.
9) Is network segmentation and traffic control appropriate?
Concerns remain even if vulnerabilities are remediated since new vulnerabilities are discovered every day that allow intrusion and compromising of administrator privileges. Therefore, it is desirable to segment the corporate network so that it does not allow attackers to penetrate deep into the network. This can be achieved by separating VLANs and installing a firewall between them to limit communication between VLANs. This is especially important in segmentation of the network where important data and backup are stored.
10) Is sufficient threat detection capability implemented?
So far we have discussed defense, but it is better to think that intrusions cannot be completely prevented. Once compromised, the attacker explores the corporate network and prepares for attacks. Anti-virus software that detects known malware is not enough to detect the movement of such attacks.
It is possible that attacks will slip through next-generation anti-virus software with enhanced detection, so it is desirable to introduce Endpoint Detection and Response (EDR) that detects threats by analyzing OS and kernel logs. Yet, EDR is not effective enough just by installing it; only by establishing operation will it show its true value. If there is any difficulty in establishing operation, we recommend using a service such as a “Managed EDR Service”.
11) Can you contain threats?
With EDR widely deployed in corporate networks, it will be easier and faster to investigate how widespread detected threats are.
It is necessary to be prepared to contain threats by identifying the compromised VLAN and making it inaccessible to other VLANs. It shows how important segmentation is here as well.
12) Can you identify the signs of an attack?
Once improving upon the ability to detect and respond, also consider using threat intelligence to identify signs for attacks.
We would encourage to start with open threat intelligence or threat intelligence provided by already-relevant security vendors and be prepared to answer the following questions:
- Which cyber-attack groups are considered to aim at the country, industry, or company you are in?
- What tactics or techniques could be used and are you ready for them?
- Can you detect the signs that the attacker launches an attack in your environment?
13) Are you trained and tested against attacks?
When security has been enhanced to the targeted level, what comes next is training to improve user awareness as well as penetration testing to check for system security measures.
The cycle of continuous improvement should be established by gathering feedback and the results of activities, making further refinements to the overall security profile.
Conclusion
We have comprehensively introduced preparations for ransomware attacks above, but it takes time and money to be fully prepared. However, considering the impact of damage, the threat of ransomware is a management issue that should be developed even if it takes time and money.
First of all, let’s aim for a system that can be restored in case of damage. Next, let’s improve in the short, medium, and long-term, including other preparations. If you are interested in our consulting or solutions, please feel free to contact us.










