
On February 4, 2022, NRI Secure launched a new service, Access Check Essential, that supports the first step towards privileged identity management.
“Access Check Essential” is offered at an affordable price by focusing on “access control” and “trail recordings”, which are indispensable for access management, alongside our privileged identity management solution “SecureCube Access Check”.
In this article, we will explain the steps to realize privileged identity management and the difficulty of introducing the privileged identity management solution. Also discussed is the Access Check Essential, focusing on the core functions related to access control as the first step of privileged identity management.
4 Steps to Realize Privileged Identity Management
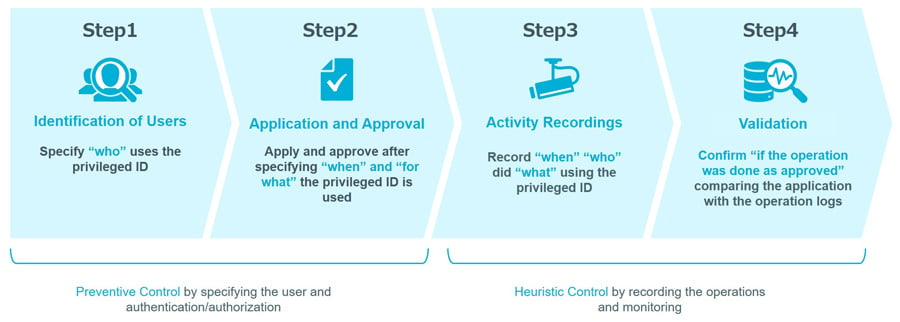 Figure 1: 4 steps to realize privileged identity management
Figure 1: 4 steps to realize privileged identity management
With the rapid expansion of remote work and advancement of IT utilizations, such as the cloud, IT control is indispensable for ensuring and maintaining security.
Above all, managing “privileged IDs” that can change information systems and access important data is one of the requisite security measures to prevent the spread of damage caused by internal fraud and cyber-attacks. Even today, there are many cases where privileged IDs are abused, causing information leaks and serious security incidents.
Under such circumstances, strict management of privileged identities is strongly required in J-SOX’s general IT control and PCI DSS, which is the global standard of the credit card industry. Specifically, it is important to carry out the following four steps consistently.
1-1. Identification of Users
Privileged ID is often shared and used, but it is necessary to determine who actually uses the privileged ID. If the user cannot be identified, it would be difficult to investigate when malicious operation are performed.
1-2. Application and Approval
Application(s) that clarifies “when” and “for what” a privileged ID will be used should be required. The privileged ID should be available for use only with approval from the appropriate person in charge.
1-3. Activity Recordings
To ensure traceability, logs on “who”, “when”, “for what” need to be recorded for the privileged ID used. It is important to make the log searchable and record the logs to reveal operation details, so that the relevant log can be found for efficient incident response.
1-4. Validation
It is necessary to compare the contents of the application with operation logs to confirm that the operation was done according to the application, then the validity of using the privileged ID is verified.
Challenges to Introduction of Privileged ID Management Solution
A dedicated solution is not necessarily needed to perform these four steps. It is also possible to manage by email or Excel, and to formulate and implement operation rules.
However, with such a method, there is the possibility that omissions occur, rules are not followed, or the rules become an empty shell. It could simply be luck that no incident has occurred. In fact, many of the reasons for considering introducing a solution are due to the limitations of manual operation and identification through audits.
On the other hand, there are actually barriers to the introduction of privileged ID management solutions. While it is certain that effective and continuous privileged ID management according to the business flow of the organization can be realized, it is necessary to organize the business processes of onsite maintenance, operation, and design of the solution. The human resources, time required, and cost for introduction and operation, could be a bottleneck. There are quite a few companies that give up on implementation.
2-1. Trail Recording and Understanding of the Situation, For a Start
To help tackle the problems mentioned above, NRI Secure has released Access Check Essential.
This product is based on “SecureCube Access Check”, which has been on the market for over 15 years and has the largest market share (*1) in Japan for privileged ID management products. It supports the first step towards privileged ID management, focusing on “access control”, “log acquisition/storage”, and “audit support” that are indispensable functions for access control, while providing them at a reasonable price.
Access Check Essential is light weight, without application and approval features, which are the highest hurdles in design and operation. It is ready to obtain a trail of “who”, “when”, “which with privileged ID”, “what was done”, and start understanding the current operational status. Letting users know that an operation is recorded could work as a deterrent to fraudulent activities.
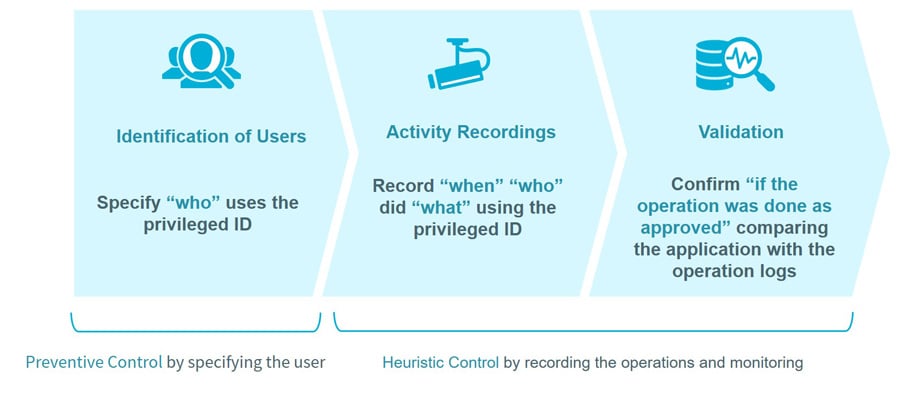 Figure 2: Small start for governance process with Access Check Essential
Figure 2: Small start for governance process with Access Check Essential
The next step is to consider introducing access control by application and approval, inventory of privileged IDs, and password management. Access Check Essential can be used to obtain a trail, grasp the current situation, and identify the issues and challenges on application and approval from privileged ID use and password management. It is a great merit that we can proceed with operational design while making improvements.
Quick and Easy Onboarding of Access Check Essential
The significant feature of Access Check Essential is its easiness of introduction.
When the “gateway method” is adopted, there is no need to install an agent (software) on the user device or managed system, it can be installed with minimal impact on the existing environment.
No distribution, introduction, or update of agents means reducing the operational load on the administrator. The workload can be further reduced by lowering the number of setting items as much as possible, which decreases the initial cost.
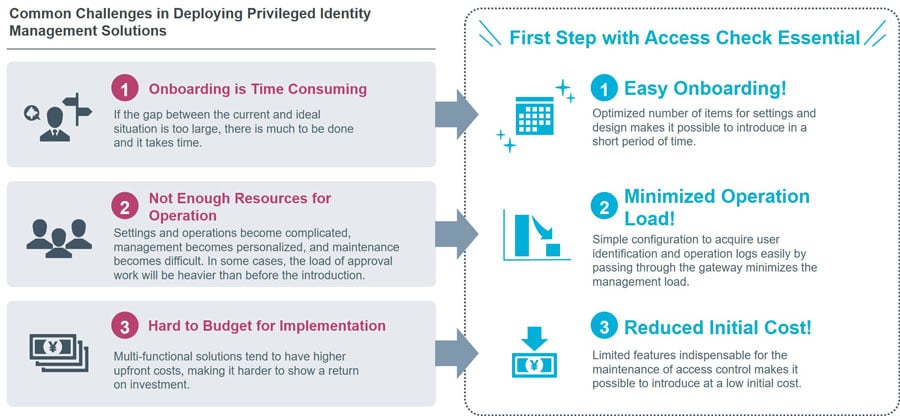
Figure 3: Overcoming the Challenges at Introduction with Access Check Essential
With the features described above, companies reluctant to introducing privileged ID management solutions can quickly take the first step toward implementation of and level up the governance of system operations and maintenance.
3 Features Essential to Access Management
4-1. Access Control
By deploying Access Check Essential as a gateway between the user device and the target system, it is possible to control (authentication/authorization) the flow of traffic. Even if multiple users share one privileged ID, Access Check Essential makes it possible to identify which user is trying to access the system/service since it authenticates the individual with the ID and password. It also authorizes whether the user can access the system based on the policy defined in advance.
4-2. Log Acquisition and Recordings
All operations performed through Access Check Essential are logged. What’s retrieved is the “access log” that summarizes the outline of access and the “operation log” that records the actual work contents. The logs are encrypted and saved, and it also has a log tempering detection function in place.
Only the auditor can see the acquired logs and becomes an effective method of proof for monitoring and internal control in internal audits.
4-3. Audit Support
Auditors can see the access status in a list by using the daily report function of the access logs. It is also possible to check from the report whether the operation logs contain keywords registered in advance, such as malicious commands.
The acquired logs can be searched with the conditions, such as date and time of use, user, access source /destination IP addresses, etc., so that the target logs can be found and investigated immediately.
Easy Upgrade to Full Featured Version
The features mentioned above alone cannot meet IT general control and PCI DSS standards. However, if you need to step up to privileged ID management that meets those criteria, you can easily move to SecureCube Access Check, which contains all the features you may need.
SecureCube Access Check has a full range of features that can manage and issue passwords for workflows and privileged IDs, enhance multi-factor authentication, and link with external systems, which makes it possible to perform stricter privileged ID management.
All data including logs and settings acquired via Access Check Essential can be migrated to SecureCube Access Check as is.
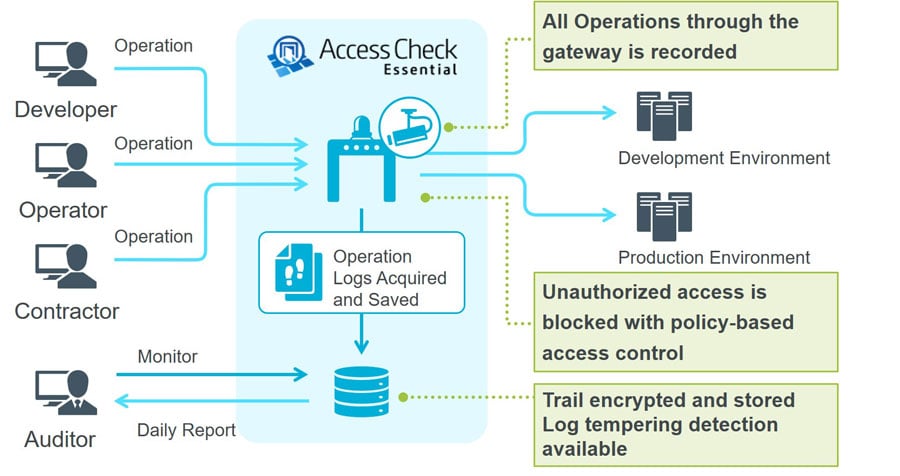 Figure 4: Access check required Usage image
Figure 4: Access check required Usage image
Conclusion
Privileged ID management, which has been mainly addressed by listed companies, has now become an important security measure, regardless of company size.
It is difficult to meet all the necessary elements for privileged ID management without knowing the current situation. First, let’s start acquiring and monitoring trails, which are relatively easy to introduce, so that you can understand who, where, and what you are doing. From there, you can take the first steps towards privileged identity management that meets IT general control and PCI DSS standards.










