
NRI Secure Insight is published by NRI Secure and includes “information security fact-finding survey” targeting companies in Japan, the United States, and Australia. The 2020 survey revealed that there is a big difference in grasping and recognition in information security of Japanese companies.
In this article, we will explain countermeasures and points for internal fraud, including specific solutions, based on differences in perception regarding security controls of outsourcers, and possible cases.
First, let’s look at how companies grasp security controls for the supply chain of affiliated subsidiaries, partners, and contractors, to examine the actual situation of Japanese corporate activities in general.
Characteristics of security measures in Japanese companies
Point 1: Insufficient understanding of security measures of outsourced companies
This survey, regarding security controls for supply chains, revealed that nearly 70% of domestic affiliated subsidiaries are grasped but 50% of domestic business partners, contractors, and overseas affiliated subsidiaries, could not be grasped.
It shows that domestic security measures are being promoted in line with the recent increase in targeted attacks and security incidents.
On the other hand, there is a tendency for less control over oversea affiliates than domestic affiliates, business partners and contractors over affiliated subsidiaries. It seems that the actual situation is not fully understood due to factors such as relationships between companies, language barriers, and security budgets.
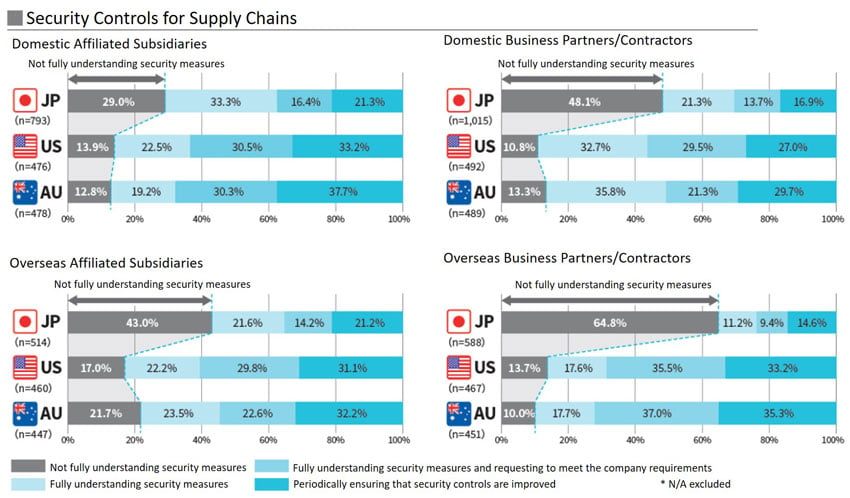
Figure 1: Security Controls for Supply Chains (NRI Secure Insight 2020)
Point 2: Internal fraud is the top threat
Next, let’s look at what Japanese companies consider as a threat.
The figure below shows that characteristically Japanese companies tend to regard “damage caused by internal fraud” and “wrong email transmission” as a threat. Alternatively, foreign countries tend to regard external attacks such as targeted and ransomware as a threat.
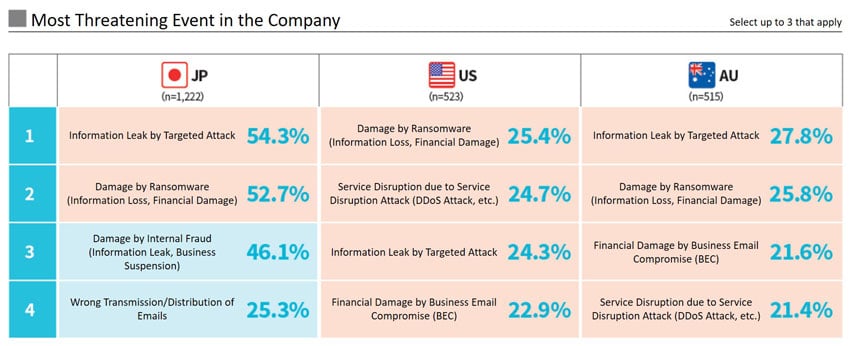
Figure 2: Most Threatening Event in the Company (NRI Secure Insight 2020)
Point 3: The trigger for security measures is a security incident
Finally, we will look at the triggers, reasons, and background for implementing security measures. The first item is “internal security incident” and the second is “top-down instruction from management”.
The ratio of top-down instructions from management has been increasing compared to the past, in addition to promoting remote work by the spread of COVID-19 and with instructions to strengthen security, but it seems there is still a strong tendency to take passive responses to actual events and incidents.
As for overseas, top-down instructions from management account for a considerable proportion and it can be said that preventive measures are taken.
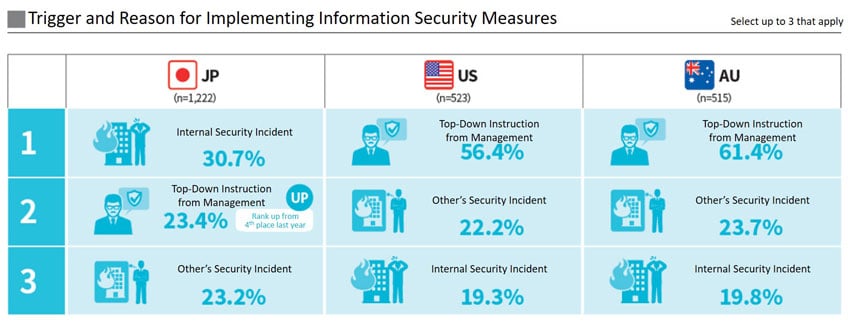
Figure 3: Trigger and Reason for Implementing Information Security Measures (NRI Secure Insight 2020)
So far, we have examined how much Japanese companies understand the security controls of contractors and the potential threats and how different the triggers for implementing security measures are.
It does not apply all companies, but as a tendency of Japanese companies, we observe that:
●many companies do not fully understand the security controls of overseas affiliated subsidiaries, domestic and overseas business partners, and contractors●they feel that internal fraud is a threat, but as a response, it has become a post-incident (passive) matter
Cases of Internal Fraud
What internal frauds can occur under the circumstances mentioned above? I would like to highlight a case to explain further.
Fraud by outsourced employee in charge of system management
An employee of an outsourced company that conducted system management for development, maintenance, and operations for company A, obtained customer information, including ID and password from their production environment, and transferred it to a private email address. After that, he illegally accessed the website of company A and withdrew a large amount of cash by manipulating the customer account. As a result, the outsourced contractor company paid damages to company A.
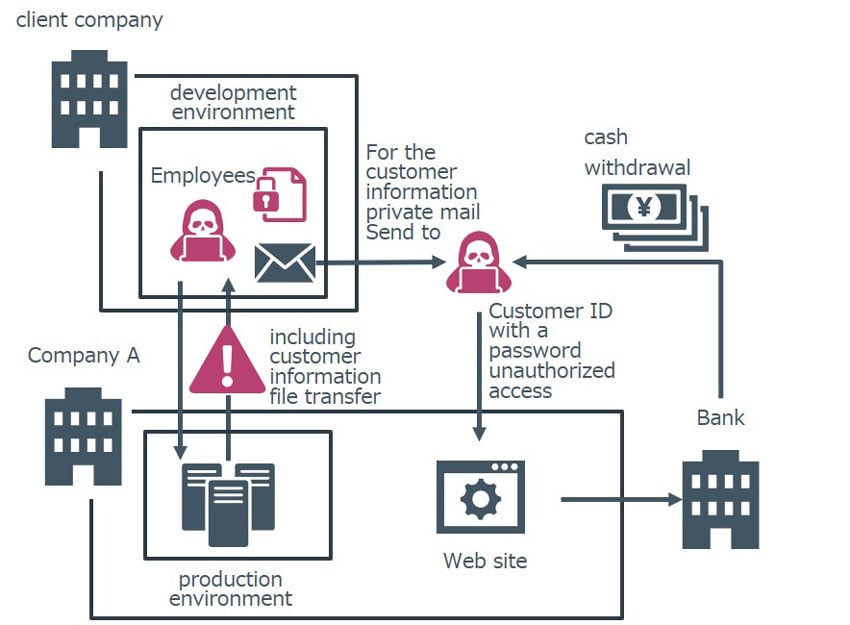
Figure 4: Internal Fraud Case Overview (Summarized from the press release at the time of incident occurrence with our guess)
In this case, it is considered that company A and the contractor could have avoided the issue if access control, log monitoring, enforcement of security rules, identity verification, etc. were properly implemented where necessary.
Now, from the perspective of company A, let’s observe and sort out points by focusing on the routes and environments in which the contractors had the direct access to the production environment of company A.
The points on the routes and environments to access production environment are the followings:
- Point 1: The employee had permission to access the production environment
- Point 2: The employee was able to transfer files containing customer information from the production environment
- Point 3: The confirmation of file contents by the administrator was not performed sufficiently
These factors resulted in the contractor being able to access the production environment of company A, making it possible that the incident occurred in which the customer information was taken out.
So how could control be implemented to detect and prevent the fraud?
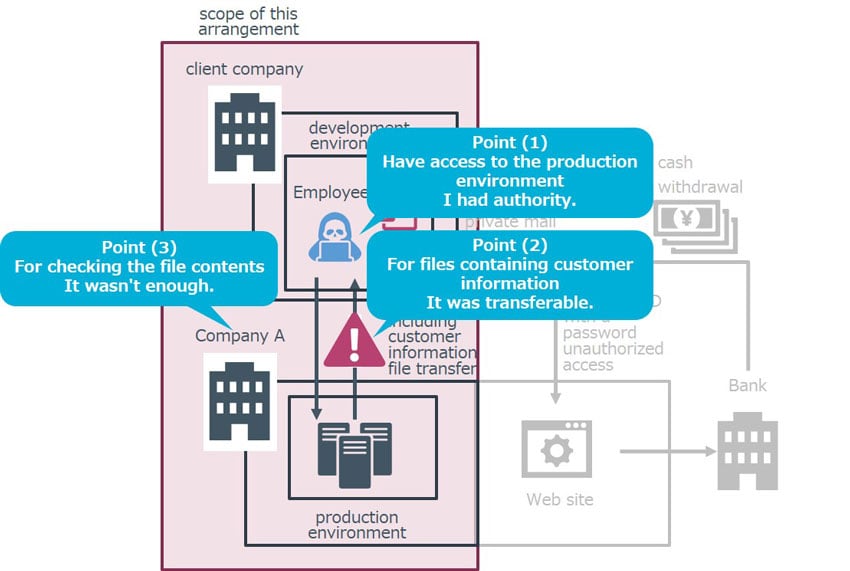
Figure 5: The points on the access to the production environment
Security Measures against Internal Fraud
It is considered that there are 3 security measures for accessing the production environment and taking files outside of the organization in this case as follows:
Access control by application/approval workflow
- Restrict access to the production environment without request and approval process
- Force user ID and password be changed each time for access to the production environment
An administrator ID with more privileges than a normal user in a production environment, also called privileged ID, can lead to leakage of important information if it is used improperly within the internal network.
By taking the measures listed above, it is possible to prevent unauthorized access of the production environment of point 1, and prevent unauthorized use of the privileged ID.
Control and detection of file outflow
- Detect files transferred which are not authorized for transfer
- Restrict protocol execution for file transfer
It is important to take measures to prevent files and information containing customer material from being leaked. With the measures above implemented, it is possible to control file transfer itself of point 2, detect unauthorized file transfer and prevent unauthorized access in the organization.
On the other hand, there may be cases where a file containing customer information slips in legitimate transfer with approval and transferred fraudulently.
Detection of files containing important information
- Check the contents of the file to see if it contains important information such as customer information
This measure is effective when customer information is mixed in when a legitimate file is transferred. Even if a file containing important information is transferred in point 3, it is possible to check the contents of the file and detect it, which helps response when an incident occurs.
By taking multiple measures as described above, confidential information, including customer information, will not be transferred. Even if it is transferred, it can be detected.
Effective Solutions against Internal Fraud
So far, we have organized security measures for the case, but is it possible to manage these operations? Access control by application/approval workflow is feasible, but it is easy to imagine that checking the contents of transferred files can be burdensome. In that case, it is possible to efficiently prevent and detect internal fraud by introducing privileged ID management products, and solutions that are effective against internal fraud.
A privileged ID management product is deployed between the company and the contractor to control employee access to the production environment. It is possible to control access to the production environment of users who are not approved, and to detect the transfer of specified files. In addition, the administrator can check logs of content operated by the employee. If a file containing important information is transferred, such as customer information, the product can detect and notify administrators. If you are considering how to deal with internal fraud, a privileged ID management product is recommended.
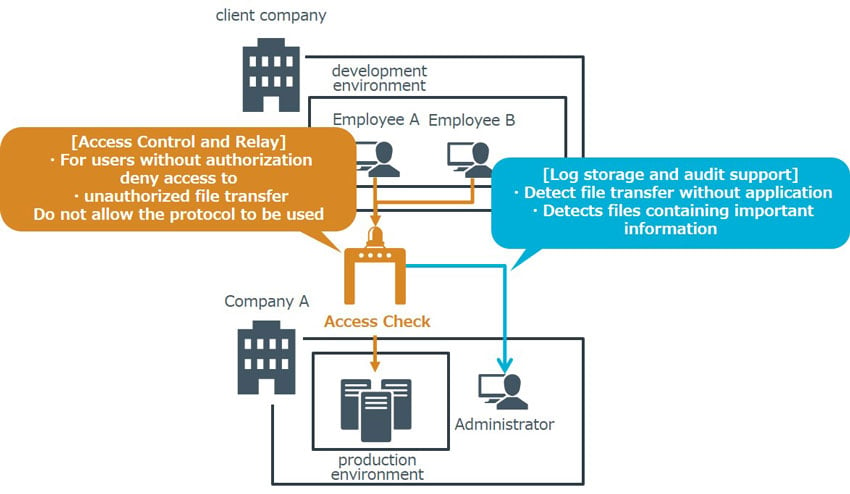
Figure 6: Effective Solutions against Internal Fraud
Conclusion
We are entering an era in which security measures are taken not only by the company, but also across the supply chain of contractors.
Information leakage and damage to end users caused by internal fraud affects credibility of the company. Privileged ID management products are effective as a countermeasure to “make crime difficult” for malicious internal users by controlling them, that they can be used only for the right users, the right purposes, at the right time.
In addition, by acquiring operation logs when using the privileged ID, it has the effect of “increasing the risk of being caught”. By incorporating them not only as rules but also as a mechanism, it can be implemented as labor saving and standardized.
NRI Secure provides a privileged ID management solution called “SecureCube Access Check” that can achieve access control and log auditing, approval workflow, and trail management for privileged IDs in a short period of time and at low cost.
As a company specializing in information security, we have been actively expanding its functions for more than 15 years. If you are about to decide or have concerns on the implementation of privileged ID management product, please feel free to contact us.










