
In recent years, with advancing digital transformation, collaboration between companies or systems have been speedy. At the same time, attacks that exploit security on supply chains and networks that connect headquarters with group companies, overseas bases, contractors, business partners, etc. are on the rise. In many cases, security incidents that actually occur in other organizations impact the entire supply chain, leading to the suspension of supply to the market and leakage of important information.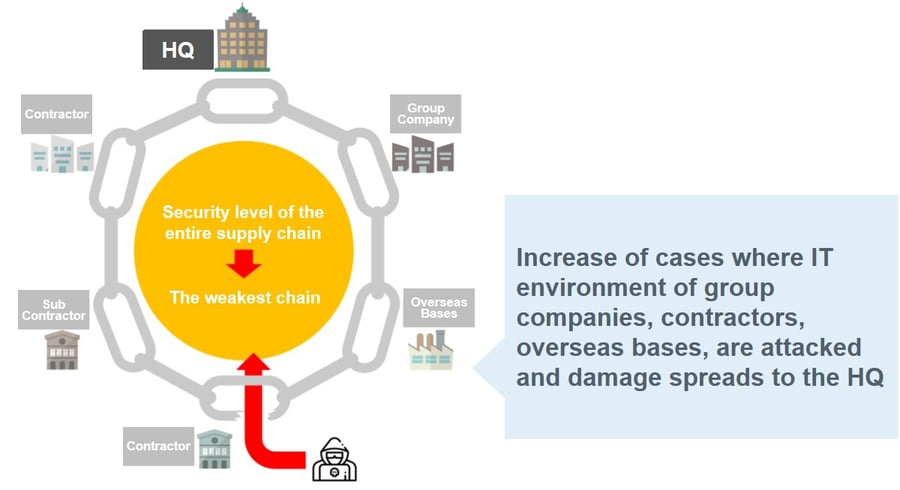
Strengthening your own security measures is no longer enough and the companies that your supply chain consists of need to maintain a certain level of security. It is important the company controlling the supply chain plays an active role.
In this article, we will explain the situation surrounding supply chain security and the four initiatives that companies in the position of controlling the supply chain should take to strengthen it.
The Situation Surrounding Supply Chain Security
The defense industry is a good example when starting security measures for the supply chain. They have long placed great importance on the handling of confidential information and have paid close attention to attacks from malicious attackers who are trying to steal confidential information.
As the supply chain surrounding the defense industry has become huge and complicated, the security measure levels of related companies that make up the supply chain has varied. It has resulted in attackers moving their targets from large enterprises and government agencies with robust security measures, to companies with inadequate security, indirectly stealing important information. In fact, there have been cases of information leaks from companies with insufficient security measures.
In response, there is a movement to strengthen supply chain security controls by enforcing compliance with “NIST SP800-171” upon the business partners in correspondence with the U.S. Department of Defense (hereinafter referred to as “DoD”) to protect information provided by DoD.
Similarly, Japan’s Ministry of Defense has developed a new information security standard, the Defense Industrial Cybersecurity Standard, which incorporates the same level of control measures as NIST SP800-171, and contracts from fiscal 2023 onward will be required to apply this standard. (Refer: https://www.mod.go.jp/atla/cybersecurity.html)
Other industries also have their own industry-specific regulations and guidelines, so it is desirable to work towards compliance with them first. On top of that, it is recommended to refer to the efforts of the defense industry in strengthening the security of the supply chain.
In other words, to ensure that the entire supply chain is above a certain level of security it is essential for the outsourcer to:
- Establish supply chain control policy
- Understand and manage the status of security measures in accordance with the security control policy
- Promote raising the level of security measures
Furthermore, it would be desirable to prepare a backup plan for important business partners in case risk is revealed.
4 Strategies to Strengthen Supply Chain Security
So, how should a company in position to control the supply chain strengthen security with awareness of the entire supply chain? Of course, compliance with industry-specific regulations and guidelines, such as the NIST SP800-171 and defense industrial cybersecurity standards mentioned above, are also required.
As an initiative focusing on supply chain, it is recommended to control the security of the supply chain by responding to the following four points, as well as maintaining the level of security measures at companies related to the supply chain at a certain level or higher.
The details of each item are as follows:
Control Policy and Definition of Supply Chain
It is very difficult to strengthen security for all supply chains surrounding the company. Companies that control the supply chain must first classify the parties involved and define the scope of application. Points to consider in classifying are the importance of the products and services provided by supply chain companies, whether they can be substituted, and the transaction amount.
Then it is recommended to define the overall security control policy, such as the risk assessment to be used according to classification, visualization method for the status of security controls, and the required security levels. For the classification and control policy of supply chain related companies, it is also effective to take concepts of existing frameworks and guidelines into consideration in light of the current situation for the supply chain surrounding the company.
If there are concerns about how to effectively use supply chain classification policy, frameworks and guidelines etc., we can support you with our consulting services such as SCM Advisory Support and SCM Assessment Support.
- Available Service: SCM Advisory Support, SCM Assessment Support
Visualization of Security Controls
It is necessary to visualize and manage the actual status of security measures for each company according to the classification of supply chain related companies. In addition, it is desirable to consider and organize how detailed the situation should be grasped, the follow-up system, and whether or not the person in charge should cooperate, etc., according to the classification defined in the previous section.
NRI Secure offers multiple services to visualize and organize the status of security measures for group companies, overseas bases, contractors, business partners, etc. The optimal service will differ depending on your company's unique needs, such as the scale of your supply chain and the importance of the information being handled, so please contact us first.
- Available Service: Visualization Service of Security Measures, Global Security Assessment, Secure SketCH, Auto Assessment (SecurityScorecard-linked), GR360
Promotion of Implementation
If the results from visualizing security measures of supply chain companies reveal that the measures are insufficient, it is necessary to promote the strengthening of additional security measures, ask supply chain companies to strengthen their countermeasure based on reports, and check the countermeasure status regularly.
In particular, the company that controls the supply chain cannot one-sidedly request business partners to strengthen countermeasures, as it is difficult to support the cost of implementation. In such a case where countermeasures cannot be implemented in time due to budgetary constraints, it needs to be considered that a certain grace period is set before completion, while stating that the countermeasures and improvement plan is part of the requirements for continued business.
Review of Control Policy
Even though a supply chain security control policy is defined, it does not always remain optimal. A PDCA Cycle (Plan-Do-Check-Act Cycle) is required to evaluate whether the current supply chain security control policy is effective by visualizing the actual security situation, promoting security measures, and to make improvements as necessary.
It is also necessary to update the control policy in line with current industry-specific regulations and guidelines, recent changes in cyberattack trends, and the emergence of new standards. Evaluating supply chain security controls using appropriate frameworks and guidelines is also useful.
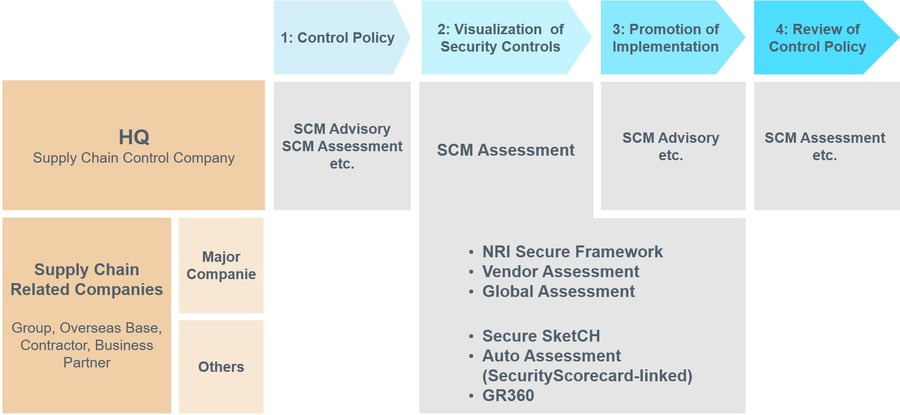
Figure: Available services adaptable in various situations
Conclusion
In light of the recent intensification of cyberattacks targeting supply chains, laws and regulations that require security measures considering the entire supply chain are being strengthened, especially in the Unites States. Companies, products, and services that do not meet the requirements may be restricted from participating in the supply chain.
In Japan, the development of “Defense Industry Cybersecurity Standards” has progressed, mainly in the defense industry. The same trend has been followed elsewhere, such as the “Information Security Standards for Procurement of Equipment and Services” being renewed. Companies involved are forced to strengthen their countermeasures.
NRI Secure provides multiple services, including consulting support for supply chain security measures. If you are considering strengthening the security of your supply chain, or if you are facing problems such as not knowing what to do and where to start, please do not hesitate to contact us.










