
Author: Masayuki Nakada, IT Security Analyst
Since the COVID-19 pandemic started, working from home (WFH) has become more common for many companies. The Japanese government recommends WFH as a “new normal” that is different from pre-COVID-19 pandemic. I have switched to WFH since early April 2020 and at the time of writing this article (late June 2020), I have been able to continue working without ever coming to office. I can understand its potential.
Now, when in WFH situations, it is necessary to connect to internal systems of the organization by some means, but recently, utilizing a VPN (virtual private network) connection is probably the most popular method. Once the remote device connects to the VPN, it is recognized as a part of the corporate network and it is possible to directly access the internal system. It also enables defense in depth by the internal network security.
With the capability of monitoring the logs of network security devices, it is possible to quickly detect signs of an incident. So, you can say, a VPN is a convenient mechanism that achieves secure remote connection, but on the other hand, it has a disadvantage that incident response in the event of malware infection, etc. may become difficult.
In this article, we will explain the issues and countermeasures for endpoint security during WFH, referring to the incident cases that had actually occurred in WFH environments.
WFH environment
First, here is the system environment before discussing the incident case.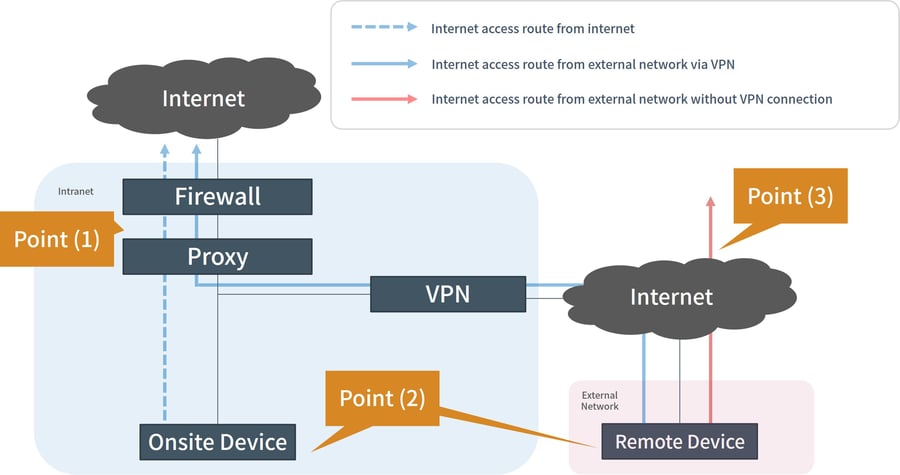
There are 3 points to pay attention to about this environment:
- Point 1
Security products such as firewalls and proxies are installed on the internal network route to acquire logs and control access. When an incident occurs, the impact is investigated by log analysis and remediation by access control is implemented.
Point 2
Security software such as anti-virus, asset management, and access control of USB devices are install in the remote device.
Point 3
While connecting to a VPN, connection to the internet is routed via the internal network. When not connected to a VPN, it can be connected to the internet directly.
The structure of system like above is generally used in the real world and there are many cases where it is operated in the similar way.
What kind of incident occurred?
The incident introduced here begins when the remote device used during remote work was infected with malware. The following is the timeline.
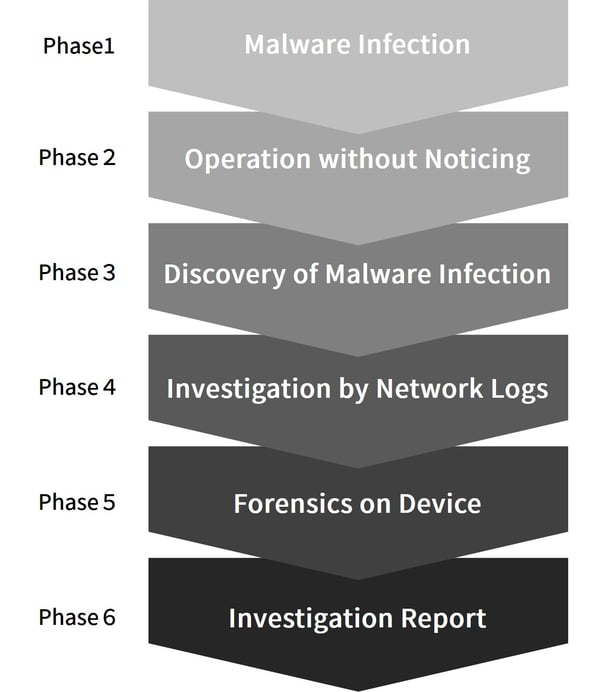
- Summary of incidents that occurred in the remote work environment
- Phase 1: Malware Infection
- While a user was away from the device in for 30 minutes, VPN connection was disconnected without the user’s knowledge. Disconnected from the VPN, the user accessed the internet directly and was infected with malware while browsing a website.
- Phase 2: Operation without Noticing
- Antivirus did not detect the infection and the user continued working after reconnecting to the VPN again.
- Phase 3: Discovery of Malware Infection
- After a few weeks, a malware infection was detected after an update of antivirus definitions. The system administrator received notification.
- Phase 4: Investigation by Network Logs
- The impact was investigated by network logs. Traffic from proxy log to C2 server (attacker’s server) was found but the traffic was blocked since it matched a URL filtering blacklist. However, it remains suspicious why the time period that the traffic occurred was limited.
- Phase 5: Forensics on Device
- Network logs were not sufficient to determine the impact and forensics was conducted on the device to clarify suspicious points.
- Phase 6: Investigation Report
- By comparing the network log with the results of the forensic investigation, many infringements were confirmed during the time the device was not connected to the VPN. While connected directly to the internet, communication with C2 server occurred successfully, and it was revealed that the attacker’s infringement proceeded.
- However, there was a limit to the events that could be grasped from the trails left on the device. It was not possible to clarify the full extent of infringement by the attacker, such as whether business information was stolen or not.
Challenges on handling incident in WFH environments
There are a few issues in this case. From the perspective of “incident response” in remote devices, let’s consider the following.

Endpoint security depending on Antivirus
In this case, security control for the remote device depended on antivirus software. So-called “pattern matching” antivirus software has reached the limit of its detection capability against recent attacks, making it difficult to deal with ever-increasing malware.
Also, when not connected to a VPN, the internet can be accessed directly from the device. Protection by defense in depth with firewall, proxy, etc., which was effective via the internal network, was not utilized.
No visibility on endpoint while not connected to VPN
It is difficult to grasp the behavior and communication of remote devices without being connected to the VPN. Specifically, when malware or an attacker remotely controls an endpoint, it communicates with C2 server. If the endpoint is not connected to the VPN, logs will not be stored. Thus, it becomes difficult to investigate when the attacker’s operation was performed from the traffic logs such as proxy logs.
In addition, although logs were stored with asset management software, the main focus was on “user operations”. Malware and remote-control behaviors by attackers were not recorded in the logs.
Prolonged forensic time and technical limits
Forensic investigation was conducted by clarifying the event, accumulating traces of the attack remaining on the OS as points, and connecting them as a probable line. Unfortunately, it was difficult to reveal how the infringement occurred with the limited traces available due to the elapsed time from incident occurrence to incident discovery.
To deal with this situation, the behavior is usually inferred by comparing security device logs (especially the proxy logs) with the forensic investigation result of the device. However, in this case, there was no log left during the period of direct connection to the internet. Despite the large amount of time spent in investigation, the findings were limited.
Endpoint Enhancement with EDR
As a solution to solve the problems explained above, EDR (Endpoint Detection and Response) is being introduced by companies. EDR is a solution that assumes that an incident, such as malware infection, will occur. It will be a tool that strengthens the “investigation” and “response” when an incident occurs.
The following are benefits of introducing EDR and the explanation of how the above-mentioned issues will be solved when EDR is introduced.

Endpoint monitoring based on behaviors
EDR can record the events that occur on the endpoint at the process level and detect when an operation that seems to be caused by malware or an attacker is performed.
In addition, many EDR solutions also have antivirus capability and by enabling this, it is possible to implement advanced security features.
Endpoint protection anywhere
Many EDR solutions are cloud-native solutions and can be managed as long as the device connects to the internet. Even while not connected to VPN, which was a problem, detailed logs such as generated processes, created files, and communication destinations, are accumulated in the cloud environment. That makes the investigation easy and smooth even if there is suspicious behavior.
Also, during remote work, it is not easy to physically seize the device. With EDR, a suspicious device can be logically isolated from the network, making it easy to take primary action and prevent the spread of infection.
Now, you may ask “what if the device always keeps the VPN connected?” In many cases, the connection disconnects automatically due to issues, such as the load on the network and equipment.
Improved analysis accuracy and speed at forensics
In traditional forensic investigations, after seizing the device, a process such as “evidence preservation” with data copy takes a considerable amount of time (about 1-2 days) to conduct. EDR does not require such processes and can be investigated based on readable logs stored in the cloud.
There are also significant advantages that traditional forensics do not have, such as “the behaviors on the device becomes clearer in chronological order” and “it is easy to investigate multiple devices at the same time”.
Conclusion
Until now, the focus of security measures in organizations have been based on “network-type defense in depth” and “log acquisition at endpoints”, which have not penetrated deeply. However, now that remote work is common, there is an increasing need to improve the security levels of endpoints.
We provide “managed EDR service” which is an operation support service of EDR. We have seen cases where the safety of endpoints dramatically improved by introducing EDR, and response loads in the event of an incident have been reduced. No serious incidents have occurred for customers who introduced managed EDR as recommended by us. If you would like to know more about EDR, please feel free to contact us.










