
Author: Jun Yano,
Information Security Consultant (CISSP, CISA)
On December 19th, 2023, the NSA (National Security Agency) released the "NSA 2023 Cybersecurity Year in Review[i]". This document outlines their initiatives and achievements in cybersecurity throughout 2023. While it appears to be a performance report for the NSA, it holds significant value for understanding where the United States, as a leading nation in cybersecurity, has been allocating its resources and its vision for the future. This blog will highlight some of the topics extracted from the "NSA 2023 Cybersecurity Year in Review", accompanied by my own insights.
Cybersecurity Initiatives for Supply Chains
Firstly, the NSA is responsible for protecting and defending the following entities and their IT systems:
|
NSS(National Security Systems) |
These networks contain classified information or are otherwise critical to United States military and intelligence activities. |
|
DoD(The Department of Defense) |
U.S. Military services and combatant commands as well as U.S. government agencies and departments related to national security. |
|
DIB(The Defense Industrial Base) |
The ever-growing group of companies that design, develop, operate, and maintain the Department of Defense’s critical systems, platforms, and technologies required to defend the nation. |
The NSA has provided various forms of cybersecurity support to these entities. Among these supports, one of the most distinctive initiatives is the assistance provided to the DIB, which forms the supply chain of the DoD. This initiative is detailed in the "Partnering" chapter of the NSA's review. The NSA has already provided cybersecurity assistance to over 600 organizations within the DIB. According to the NSA's review, more than 70% of the DIB consists of small businesses, many of which may lack the resources to implement cybersecurity protections independently. This prompted the NSA to provide following solutions to them at no charge.
|
Protective Domain Name System |
This system blocks users from connecting to malicious or suspicious domains, thereby reducing risk and safeguarding DOD information. |
|
Attack Surface Management |
This involves providing vulnerability scanning to assets detected by perimeter scans using Open Source Tools and located on internet-facing networks. |
|
Threat Intelligence Collaboration |
This initiative entails providing non-public, DIB-specific threat intelligence information to DIB organizations. |
We also offer Attack Surface Management and Threat Intelligence solutions to our customers. However, these solutions have not yet gained widespread adoption, especially among small businesses. The availability of government-driven initiatives like these to all DIB organizations underscores the importance of strengthening cybersecurity within the supply chain for U.S. national security.
In addition, the NSA has launched the following four new pilot solutions. This announcement highlights their active adoption of new cutting-edge technologies.
|
Cloud Security |
Provide security assessments for vulnerabilities and misconfigurations of cloud systems used by DIB organizations. |
|
Threat Hunting |
Identifying and mitigating threats before they cause harm involves actively providing a system information and event management platform to DIB partners to facilitate the detection and mitigation of malicious and suspicious network activity. NSA analysts will hunt alongside the DIB partners and will develop threat-hunting guides and analytics to distribute throughout the DIB. |
|
Phishing Protection |
Provides DIB customers with a secure email gateway to filter phishing attacks, along with access to a sandbox to better understand any malware associated with the malicious attachments to enable appropriate mitigation development. |
|
Autonomous Penetration Testing |
This pilot innovatively leverages automated tools, algorithms, and AI to identify digital vulnerabilities more continuously than human capabilities. Mimicking the actions of hackers, this testing provides real-time threat assessments to reduce human intervention, increasing efficiency and providing a more insightful view into how our adversaries are thinking. |
Some may find it unfair to receive these government-assisted solutions at no charge. However, it's important to acknowledge that DIB organizations must still invest resources to prepare for the implementation of these solutions and to effectively respond to alerts generated by them. Additionally, it's crucial to recognize that the scope of these assistance programs is limited to the DIB-related area. Therefore, they cannot entirely replace the overall security initiatives of your company.
Warfare in Cyberespionage
In the chapter titled "Vigilance," the NSA outlines their responses to cyber-attacks perpetrated by nation-state threat actors, as well as their collaborations with other countries. Collaborating with external entities has been vital because physical borders can’t be any restraints when it comes to cyber-attacks. Therefore, these cross-border collaborations have become more active recently.
Engagement against People's Republic of China (PRC) State-Sponsored Cyber Attacks
Throughout 2023, extensive coverage of the activities of PRC-linked state-sponsored actors dominated news headlines. Collaborating with international and industrial partners, the NSA took actions against the PRC-linked state-sponsored actors known as "Volt Typhoon," who targeted critical infrastructure within the United States. These actors not only utilized specially-crafted tools but also employed the technique known as "living off the land," enabling them to achieve similar results as specially-crafted tools produce by utilizing built-in network tools. This technique makes it difficult for monitoring systems like EDR to detect their activities automatically because they only utilize ordinary softwares. In response, the NSA collaborated with international partners to issue an advisory titled "People’s Republic of China State-Sponsored Cyber Actor Living off the Land to Evade Detection[ii]" in May 2023. This advisory not only outlines methods for detecting "living off the land" activities but also provides details on the commands used and examples of signatures for detection.
Additionally, the NSA confirmed a zero-day attack against Citrix perpetrated by another PRC-linked state-sponsored actor known as "APT5"[iii]. Despite targeting multiple Defense Industrial Base (DIB) companies, the NSA succeeded in protecting them by promptly detecting and sharing information about the attacks with DIB companies.
Furthermore, to raise awareness about the threat posed by PRC-linked state-sponsored actors such as "BlackTech," the NSA released the advisory "People's Republic of China-Linked Cyber Actors Hide in Router Firmware[iv]" in September 2023, collaborating with the Japan National Police Agency and the Japan Center of Incident Readiness and Strategy for Cybersecurity. "BlackTech" possesses the capability to modify router firmware without detection, initially infiltrating international subsidiaries and subsequently attempting to breach the parent company's network from within these subsidiaries. This method has been employed in repeated cyber-attacks against companies in East Asia and the United States.
Shutdown of Russian Cyberespionage Malware Infrastructure
The NSA also successfully dismantled the cyberespionage malware known as "Snake[v]" In addition to partnering with agencies within the U.S. such as the FBI, the NSA collaborated with counterparts in the Five Eyes nations, including Canada, Australia, New Zealand, and the UK. This collaboration led to the successful attribution of Snake operations to a known unit within Center 16 of Russia’s Federal Security Service. Codenamed "Operation Medusa," this operation utilized counter-hack software called "Perseus," developed by the FBI. Operation Medusa effectively disabled the infrastructure supporting “Snake”. However, it is still staggering to note that until its shutdown, this malware had infiltrated over 50 countries for nearly 20 years and had been utilized for Russia's cyberespionage activities without interruption.
Advisory to highlight Social Engineering Activities By North Korea
The NSA, in collaboration with the Republic of Korea’s National Intelligence Service and National Police Agency, released an advisory titled “North Korea Using Social Engineering to Enable Hacking of Think Tanks, Academia, and Media[vi]” in June 2023. This advisory aimed to alert personnel employed by research centers, think tanks, academic institutions, and news media organizations in South Korea and the U.S. to the rising threat of social engineering activities by Democratic People’s Republic of Korea (DPRK) state-sponsored cyber actors. According to the advisory, multiple groups of state-sponsored cyber actors, including “Kimsuky,” “Thallium,” “APT43,” “Velvet Chollima,” and “Black Banshee,” conducted large-scale social engineering campaigns aimed at gathering political, military, or economic information related to the national security of the DPRK. The advisory outlines their frequently used methods, red flags, and provides examples of actual messages found in fabricated emails to enhance awareness about social engineering attacks among potential targets.
Security for AI
The NSA has established a new entity called the "Artificial Intelligence Security Center," which specializes in securing AI technology. This organization assists NSS and DIB in securely utilizing AI technology and provides best practices and guidelines to explain how AI can be abused in cybercrimes, as well as how it can be targeted. In November 2023, the NSA published "Guidelines for Secure AI System Development[vii]" to provide security guidance for system developers using AI technology. Though not yet included in this annual review, the NSA also published "Engaging with Artificial Intelligence (AI)[viii]" in January to promote the secure use of AI technology.

Source: https://www.nsa.gov/Press-Room/Press-Releases-Statements/Press-Release-View/Article/3523329/nsa-us-federal-agencies-advise-on-deepfake-threats/
Furthermore, in cooperation with the FBI and CISA, the NSA released a document titled “Contextualizing Deepfake Threats to Organizations[ix]” in September 2023 to warn about the risk of abusing deepfake technology and to present ways to mitigate it. In this document, all businesses are encouraged to prepare for these threats, as phishing attacks utilizing deepfake technology falsify not only messages but also voices and videos to deceive victims. This document introduces the followings as major risks of deepfake technology.
- Executive impersonation for brand manipulation
- Impersonation for financial gain
- Impersonation to gain access
The document also highlights a real case in which a UK company was defrauded of $243,000 using deepfake audio. Generally, countermeasures for deepfake can be categorized into “Detection” and “Authentication.” Some public organizations such as DARPA (Defense Advanced Research Projects Agency), AFRL (The Air Force Research Lab), and CAI (Contents Authenticity Initiative), along with private companies like Google, Microsoft, and Intel, have already been working on the development of these countermeasures. The document explains and organizes multiple countermeasures, so I encourage you to review it if you are interested. However, I found it quite challenging for companies to implement these countermeasures individually, especially in terms of “detection,” due to both technical and operational complexities. Therefore, my recommendation is to implement and maintain general countermeasures for phishing attacks, as they are expected to mitigate the threats listed above (No. 2 and No. 3). Companies may also consider waiting until new countermeasures for deepfake technology become more widespread and are adopted by large platforms and product suppliers for video conferencing and streaming.
Threat of Quantum Computing
Some researchers have pointed out that public-key cryptography technology, currently used globally, may become vulnerable due to the advancement and development of quantum computing, which greatly outperforms existing computers. However, the development of CRQC (Cryptographically Relevant Quantum Computer), which would enable us to decrypt information encrypted by public-key cryptography, has not yet been completed and appears to require more time for its fruition.
In the United States, NIST has been leading the project to select a Post-Quantum Cryptographic Standard, and the selected standard is scheduled to be announced in 2024. According to the press release from NIST in July 2022, four algorithms — "CRYSTALS-Kyber," "CRYSTALS-Dilithium," "FALCON," and "SPHINCS+" — remained in the selection process at that time.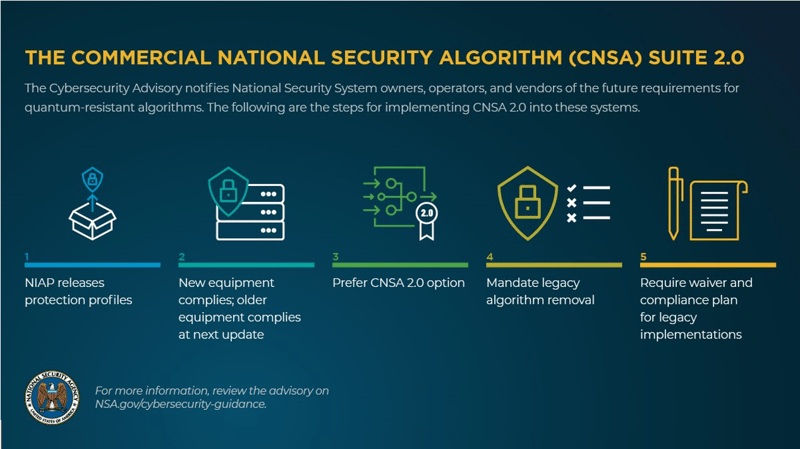
Source: https://www.nsa.gov/Press-Room/News-Highlights/Article/Article/3148990/nsa-releases-future-quantum-resistant-qr-algorithm-requirements-for-national-se/
After U.S. President Biden signed the "National Security Memorandum on Promoting United States Leadership in Quantum Computing While Mitigating Risks to Vulnerable Cryptographic Systems[x]" in May 2022, the NSA, as the National Manager for National Security Systems (NSS), has been supporting the transition and migration to Quantum-Resistant Cryptography for over 50 U.S. departments and agencies that own or operate NSS.
The report titled "QUANTUM-READINESS: MIGRATION TO POST-QUANTUM CRYPTOGRAPHY[xi]" published by the NSA, CISA, and NIST in August 2023, recommends that all businesses begin working on their migration plans, including a roadmap and inventory, immediately, even though Quantum Computing is not an imminent threat at the moment. Although the year of 2030 is considered a milestone for the due date, setting priorities for this migration is still challenging for businesses due to the uncertainty surrounding both the completion of CRQC development and the Post-Quantum Cryptographic Standard.
However, even in such ambiguous circumstances, I still recommend that major businesses expected to significantly impact the economy when the threat materializes, such as financial institutions and companies operating critical infrastructures, should initiate preparations, such as establishing project teams, creating inventories of existing IT systems using public-key cryptography, and engaging with product and solution vendors before the release of the Post-Quantum Cryptographic Standard by NIST in 2024.
Cybersecurity in Space Development
This is not much detailed in this annual review, but it's noteworthy that the NSA contributed to the development of the "Proliferated Warfighting Space Architecture (PWSA)" in collaboration with the Space Development Agency (SDA). In April 2023, SDA successfully launched the first 10 satellites constituting PWSA, followed by another successful launch in September. Presently, there are over 20 satellites operating in outer space as part of this initiative. Upon completion, the project aims to deploy over 1,000 satellites forming a mesh-type optical network. This network will offer low-latency data transport and missile warning/tracking capabilities to ground and sea-based warfighters.

Source: https://www.sda.mil/space-just-in-space-development-agency-to-award-first-satellite-contracts-by-august/
SDA also announced the successful completion of the first communication test between space and the ground in November 2023[xii]. It's evident that this communication infrastructure is crucial for national security, prompting SDA to enlist the expertise of cybersecurity specialists like the NSA. As traditional battlefields expand, the demand for cybersecurity across these domains will undoubtedly increase.
Diversity in Cybersecurity industry
According to the "NSA 2022 Cybersecurity Year in Review[xiii]", women constitute 25% of the cybersecurity workforce. The Cybersecurity Collaboration Center (CCC) at the NSA offers the training program known as "Women Immersed in NSA Cybersecurity (WIN-Cyber)" to encourage more women to pursue careers in cybersecurity. This initiative, launched in 2022 as a pilot program, provides participants with a week-long immersive experience collaborating with NSA professionals.
In 2023, the program invited five new schools and twenty enthusiastic students. Participants were nominated by their professors and represented their respective schools. Upon completion of the training, these participants returned to their schools as NSA "ambassadors," promoting cybersecurity awareness and opportunities within their academic communities.
Source: https://www.nsa.gov/Press-Room/News-Highlights/Article/Article/3566550/investing-in-women-in-cyber/
Additionally, the NSA's YouTube channel offers videos titled "Look Around: Women in Cybersecurity[xiv]", which feature introductions of women working in the cybersecurity industry.
Source: https://www.youtube.com/watch?v=Fcf5cRox4bs&list=PLWvkfYC3snpWOuXc2lr8Q0GPxd04V89V_
I changed my career and joined cybersecurity industry in 2002, however, I could hardly find women working in this industry at that time. It was same both in the local conferences and international conferences such as Blackhat and DEFCON. However, after approximately a decade, I was pleasantly surprised that I found a lot of women attending Blackhat conference. Now in our office, many women actively engage as security consultants and security analysts. I hope this industry will stay open to anyone who has talent and passion for cybersecurity.
In addition to WIN-Cyber, the NSA provides a wide variety of learning opportunities such as “NSA CodeBreaker Challenge” a CTF style competition launched in 2013 and in which students compete their ability of reverse engineering and low-code analysis along with realistic NSA mission-centric scenarios, and “NSA Cyber Exercise(NCX)” which contains training for U.S. service academy cadets and midshipmen teams from the senior military colleges as well as three-day cyber competition.
We also collaborates with the SANS Institute to provide "NRI Secure NetWars 2023" to students in Japan. These initiatives underscore the importance of continuous educational activities in nurturing future professionals within the cybersecurity industry.
Conclusion
As I perused topics highlighted in the "NSA 2023 Cybersecurity Year in Review," including advanced support provided by the NSA to partners and businesses forming the "Supply Chain" of national security, the emergence of not only cyberespionage battles but also new threats such as "DeepFake" and the imperilment of Public-Key Cryptography due to advancements in technologies like AI and Quantum Computing, and the networks constituted by the proliferated low Earth orbit (pLEO) constellation of satellites, I was struck by the breadth and depth of their activities. This comprehensive coverage is reflecting the increasing importance of cybersecurity across all sectors. I firmly believe that this trend will only continue to grow in significance. I eagerly anticipate witnessing the developments and innovations that unfold in the coming year, eagerly awaiting the insights offered in the "NSA 2024 Cybersecurity Year in Review."
[i] https://www.nsa.gov/Press-Room/Press-Releases-Statements/Press-Release-View/Article/3621654/nsa-publishes-2023-cybersecurity-year-in-review/
[ii]https://media.defense.gov/2023/May/24/2003229517/-1/-1/0/CSA_PRC_State_Sponsored_Cyber_Living_off_the_Land_v1.1.PDF
[iii] https://media.defense.gov/2022/Dec/13/2003131586/-1/-1/0/CSA-APT5-CITRIXADC-V1.PDF
[iv]https://media.defense.gov/2023/Sep/27/2003309107/-1/-1/0/CSA_BLACKTECH_HIDE_IN_ROUTERS_TLP-CLEAR.PDF
[v]https://media.defense.gov/2023/May/09/2003218554/-1/-1/0/JOINT_CSA_HUNTING_RU_INTEL_SNAKE_MALWARE_20230509.PDF
[vi]https://media.defense.gov/2023/Jun/01/2003234055/-1/-1/0/JOINT_CSA_DPRK_SOCIAL_ENGINEERING.PDF
[vii] https://media.defense.gov/2023/Nov/27/2003346994/-1/-1/0/GUIDELINES-FOR-SECURE-AI-SYSTEM-DEVELOPMENT.PDF
[viii] https://media.defense.gov/2024/Jan/23/2003380135/-1/-1/0/CSI-ENGAGING-WITH-ARTIFICIAL-INTELLIGENCE.PDF
[ix] https://media.defense.gov/2023/Sep/12/2003298925/-1/-1/0/CSI-DEEPFAKE-THREATS.PDF
[x] https://www.whitehouse.gov/briefing-room/statements-releases/2022/05/04/national-security-memorandum-on-promoting-united-states-leadership-in-quantum-computing-while-mitigating-risks-to-vulnerable-cryptographic-systems/
[xi] https://media.defense.gov/2023/Aug/21/2003284212/-1/-1/0/CSI-QUANTUM-READINESS.PDF
[xii] https://www.sda.mil/space-development-agency-successfully-completes-space-to-ground-transmission-from-link-16-tactical-data-network/
[xiii]https://media.defense.gov/2022/Dec/15/2003133594/-1/-1/0/0139_CSD_YIR22_FINAL_LOWSIDE_ACCESSIBLE_FINAL_V2.PDF
[xiv] https://www.youtube.com/watch?v=Fcf5cRox4bs&list=PLWvkfYC3snpWOuXc2lr8Q0GPxd04V89V_










