
Introduction
Due to the utilization of cloud services, external collaboration, and diversification of work styles represented by remote work, security measures to be implemented have also changed. The perimeter defense model (perimeter model) has been adopted by many organizations. It is a model that assumes if the inside boundary of the corporate network is kept safe, external threats such as cyber-attacks cannot invade boundaries. With this methodology, it is becoming difficult to prevent threats that are becoming more intense and diverse every day. To address these issues, Forrester Research has proposed a zero trust model as a new security concept.
In the current situation, where remote work is being actively used as a measure to prevent the spread of COVID-19 infection, many organizations are considering migrating to zero trust. This article describes a zero trust model, especially from the perspective of remote work security. First, we will touch on the technical elements that support zero trust and explain the differences from the traditional boundary defense model.
Technologies Supporting ZT Models
In this chapter, we will explain the various technologies that support a zero trust model. There are many technologies used, but in here, ID, cloud security, endpoint security, and network are the main technical elements.
ID
IDs play an important role in zero trust model, but we will explain what IDs are in the first place: the mechanism of authentication and authorization to use IDs for correct purposes, also the solutions to utilize them.
What is ID
First of all, what is an ID? There are three concepts that are often confused when considering an ID: Identity, Identification, and Identifier. Identity is defined in ISO / IEC 24760-1 as “a set of attribute information related to an entity”, not only user attribute information such as name and address, but also information such as service usage history and relationships with others. Identification refers to the act of “labeling” the target user and identifying the individual user. The label given at identification is called an Identifier.
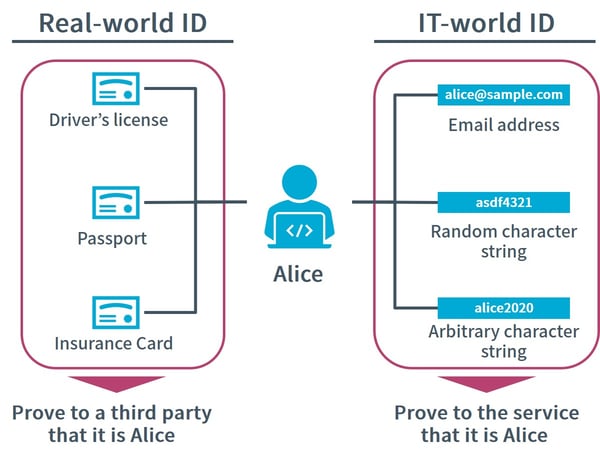
An explanation based on an example in the real world, as shown in figure 1, where a user presents a passport or a driver’s license to a service provider to confirm his/her identity when using the service in the real world. Information such as the name and address written on the presented passport or driver’s license is Identity, the act of identifying the presented user on the service provider side is Identification, and the identifier for the service provider to distinguish the user (passport number or license number) corresponds to the Identifier.
In the IT world, when using any service, it is necessary to convey the identity required for service to the service provider. It is necessary to also consider cases such as automated machines, therefore it is important how to manage the unique Identifier (hereinafter referred to as “ID” in this article) for each service.
In addition to random character strings assigned by the system and those that are arbitrarily determined by the user, there are cases where an email address is used as an ID, for there is no duplication. Also, in the digital world, there are restrictions to be considered, such as the means of linking attribute information, ensuring its authenticity, and the means of authenticating users online.
Figure1 Real-world ID and IT-world ID
ID and Authentication
From the service provider’s point of view, it is necessary to somehow prove that the ID presented is legitimately owned by the user. This proof mechanism is called “authentication”. For example, passports and driver’s licenses used as IDs in the real world includes a photo of their face. Therefore, by comparing the photo with the face of the person who presented that ID, it should be possible to judge whether the person listed in the ID and the person in front of him/her are the same. Authentication is also performed digitally, but it is not possible to authenticate with a face photo. So, authentication is performed with the following so-called three elements of authentication.
Table1 Authentication Elements and Samples
|
Authentication Element |
Samples |
|
1) Something you Know |
Password, PIN |
|
2) Something you Have |
One-time password token, Smart phone |
|
3) Something you Are |
Fingerprint, Iris |
When a user utilizes a service, the service provider presents an ID and an element for proving the ID (for example, a password). The service is provided after confirming the identity of the user. In a zero trust model, it is necessary to always confirm who is going to use the service and authentication is very important as a mechanism to secure “who”. Therefore, multi-factor authentication is recommended for more accurate authentication.
Why is it possible to perform more accurate authentication with multi-factor authentication? When authenticating with only a password, if the password was leaked for some reason, it becomes possible for a third party to spoof authentication using the leaked password, causing the reliability of authentication to be impaired. However, when requesting a one-time password token at the same time as the password, even if a malicious user who obtained the leaked password attempts to spoof authentication, the one-time password is still unknown and spoofing fails. In this way, even though the reliability of authentication cannot be maintained with only a single factor due to leakage, security can be maintained by introducing multi-factor authentication.
Authorization
Next, let us visit authorization. Authorization may be an unfamiliar word and difficult to differentiate from authentication, but in short, it means to decide whether to allow or deny an action. For example, immigration is shown in figure 2. When entering a foreign country, generally a passport is used to prove identity. This authenticates who is being examined. After that, the immigration officer decides whether the person may enter the country. This judgement is authorization.
Figure2 Authentication and Authorization in real world and IT space
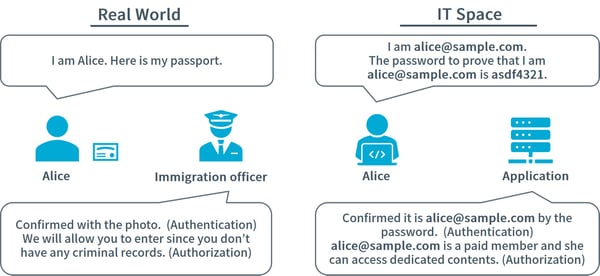
When entering the country, whether to allow entry is based on the presence of visa, criminal history, past travel history, etc. In the IT world, authorization processing is performed according to predetermined rules for determining if access to services and/or resources is possible.
For example, some smartphone applications have two versions: free and paid. The paid version can use additional specific functions. This is an authorization process that determines whether the target user is a free version user or a paid version user and allows only the paid user to access additional resources (functions) after authentication. In zero trust models, it is important to determine each time whether a user has the right to access a specific service or resource, and to create a mechanism to allow only the minimum necessary access. The authorization process, which forms the basis of this mechanism, plays a very important role.
Cloud Security
Diversification of Connecting Destinations
When it was only necessary to focus on boundary defense, there was no problem if management of servers installed in the network within the organization was focused on. However, now that it has become important for organizations to utilize them with the advent of cloud services such as IaaS, PaaS, and SaaS, servers are deployed not only inside boundaries but also on the internet. Management of these assets tend to be complicated. For a zero trust model, it is important to keep resources on the cloud safe, and we will explain some of the technologies involved.
Responsibility Boundary in IaaS, PaaS, and SaaS
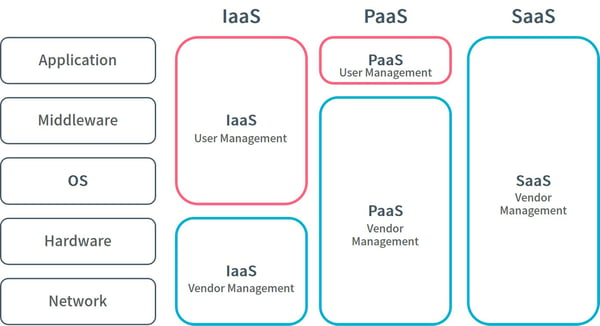
First, let us review IaaS, PaaS, and SaaS. According to the definition by NIST (National Institute of Standards and Technology), Infrastructure as a Service (IaaS) is “the function provided to users is to allocate computing functions, storage, networks and other basic computing resources, and users can implement and run any software including operating system and application on it”. The user is mainly in charge of software management and does not have to manage the infrastructure.
Platform as a Service (PaaS) is functionality provided for users to implement user-developed or purchased applications on the cloud infrastructure, which are created using programming languages, libraries, services, and tools supported by the provider. Since services such as libraries are provided on PaaS, users can develop applications using them and they mainly manage applications implemented by users.
Finally, NIST defines Software as a Service (SaaS) as “the functionality provided to users is a provider-derived application running on a cloud platform. Applications are accessed from various client devices through either a thin client interface such as a web browser (e.g. webmail) or a program interface.” On SaaS, even the application is provided to the provider, and the user does not need to manage anything other than the setting of each application.
CASB, CSPM, and CWPP Ensuring Security of Cloud Services
Figure 3 shows the above definitions and we can see that IaaS, PaaS, and SaaS have different management responsibilities for providers and users. They are easy to start and from the viewpoint of scalability, have the advantage of easy introduction to various organizations. On the other hand, since flexible configuration is available, there have been security incidents caused by misconfiguration. According to the 2020 Cloud Misconfigurations Report, between 2018 and 2019, more than 33 billion records of information leaked due to cloud misconfiguration worldwide. It was revealed that the loss is estimated at more than $45 billion dollars. So even a small misconfiguration can lead to a large loss. Even if the service is easy to use, it is still necessary to constantly check its status and ensure the reliability and safety of the service.
Tools called Cloud Access Security Broker (CASB), Cloud Security Posture Management (CSPM), and Cloud Workload Protection Platform (CWPP) are effective for checking the reliability of services such as IaaS, PaaS, and SaaS.
Figure3 Responsibility Boundary in IaaS, PaaS, and SaaS
First, CASB is a concept advocated by Gartner. Gartner defines CASB as “located between cloud service providers and cloud service consumers and inserts a combination of enterprise security policies when accessing cloud-based resources.” In short, CASB is a tool that makes it possible to use cloud applications, restrict access, and enforce organization’s security policies when using cloud applications.
CSPM is a tool that evaluates cloud security measures such as whether security policies are complied with and if there is a risk of incidents, as well as supporting settings on the cloud to comply with policies and prevent incidents.
Finally, CWPP provides a function that comprehensively supports the security of workloads in the cloud and on-premises, such as virtual machines, containers, and servers. It can perform system hardening, vulnerability management, network segmentation, firewall and communication visualization, etc.
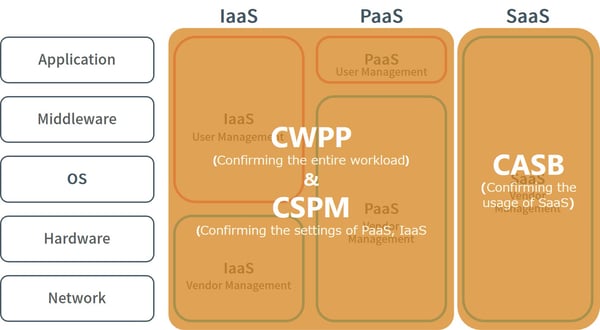
Summarizing the above, as shown in Figure 4, CASB can mainly check the usage of SaaS such as restricting access to unauthorized applications, while CSPM mainly checks the configuration in PaaS and IaaS such as status of granting administrator privileges. CWPP can check the status of the entire workload, such as preventing information leakage of containers and virtual machines. The functions provided by CASB, CSPM, and CWPP have some overlap, but each cannot cover cloud security by itself. By using these three tools in combination, visualization of the status of IaaS, PaaS, and SaaS, and the status of security measures is possible. When putting zero trust mode to practice, it is important to always confirm that the cloud service is safe to allow access by utilizing the results visualized from these tools.
Figure 4 Coverage and Features in IaaS, PaaS, and SaaS
Endpoint Security
Next, we will explain the related technologies on the endpoint that is the starting point of access. The endpoint here refers to various devices operated by the user, and specifically, devices such as a desktop or a laptop computer, a smartphone, or a tablet. In zero trust models, it is verified that the connection source device is sufficiently secure, and it is used as one factor of access control. Not limited to devices prepared by organizations, there are also cases of personally owned devices called BYOD (Bring Your Own Device) these days and how to ensure safety of devices is important.
NIST recommends “continuously monitor all devices belonging to the organization so that they are kept safe” as a measure for devices. From here, we will explain technologies called EDR (Endpoint Detection and Response) and UEM (Unified Endpoint management) to put it in practice.
EDR Monitoring Remote Device
EDR can automatically detect malware, quarantine devices, and even remove malware. Traditional anti-malware software collates with known malware databases in advance and removes malware only if they match. EDR observes the behavior on the device after the malware infects the device and removes it when it is flagged as malicious behavior.
Let’s see an example of malware detection and removal using EDR. One day, an employee who received an email and opened an attached file named “Invoice.pdf”, but the PDF file did not contain anything. In fact, the attached file was malware and was trying to communicate from the employee’s device to an external Command & Control server (C2 server). EDR detects suspicious behavior on the device and notifies the administrator of the malware infection. Upon receiving the notification, the administrator isolates the device by restricting access to the internal systems and uses EDR to remotely remove the malware.
Traditionally, when communicating with a C2 server, detection was common with a security system installed at the boundary of the organization’s network. However, in remote work, it is difficult to detect suspicious communications when there are no security control between the device and the internet. With the advent of EDR, it is possible to detect and respond to suspicious behavior at the endpoint all at once, as well as keeping the device safe regardless of location.
Security on Mobile Device
Next, we will explain the UEM used to ensure security of mobile devices. There are three main functions and the first is remote management. The administrator can grasp the status of the mobile device on which UEM is installed from the management console. For example, an employee loses a mobile device that stores sensitive company information on a train. The administrator can locate the device using the UEM administrator console, remotely wipe the device and restore factory settings.
The second function is confirming consistency with the security compliance policy; it can check whether the device meets requisite settings and status in the policy defined by the organization. For example, it is possible to check whether the PIN code is activated when the mobile device is started and whether it has been tempered with or not.
The third function is application management that manages which operation is permitted for each application in detail. It is possible to enforce policies that allow the use of applications that the organization approves, while also preventing employees from installing or running applications that are not business-related. For example, it is possible to restrict operations, such as prohibiting copying and pasting from the mail application to another application to prevent leakage of confidential information outside.
By utilizing EDR and UEM, it is possible to visualize the status of endpoints such as its status of security measures. With the results using these tools, confirming that endpoints are safe, and then permitting access is important in putting zero trust model in practice.
Network
Next, we will explain an important concept closely related to zero trust models regarding networks. There are two types of connections that should be controlled with respect to a network in a general company/organization. The first is a connection to the open internet, which is generally used to access a website publicly for conducting research necessary for business. The second is the connection to internal systems, such as browsing an internal portal or accessing the accounting system. Typically, access control of these connections were performed at the boundary of the network and segmentation within the organization, but Secure Web Gateway (SWG) and Software Defined Perimeter (SDP) have been emerging as more versatile solutions for improving network security. We will explain these two solutions that are used in zero trust model.
Protection on Connecting to Open Internet by SWG
First, SWG. SWG is a solution that is equipped with security functions such as URL filtering, virus checking, TLS decryption, and data loss protection in the cloud. It can protect web traffic from a comprehensive perspective. Unlike the perimeter model, which can aggregate communications from devices existing within the boundary to the open internet, zero trust models have challenges that communications emitted by devices cannot be aggregated into a single route.
In other words, the user will connect directly to the open internet from the device and will be exposed to threats, such as accessing websites with malicious URLs and being infected with malware. Using SWG makes it possible to perform inspections by various security functions when using the open internet.
Protection Connecting to Internal Network by SDP
Second, SDP provides access control to application and services, or more simply, a solution that provides secure connections from external devices to internal resources. In a perimeter model, when accessing an internal system from outside the boundary, it was common to use a VPN for remotely accessing the internal network. However, there are two main challenges regarding the use of VPN.
The first challenge is that the port for remote access is always open, that it is exposed to attackers all the time. Many vulnerabilities related to open VPN ports have been pointed out so far; cybersecurity incidents have been reported in which vulnerabilities were exploited to gain unauthorized access to corporate networks and encrypt information assets within the network.
The second challenge is that the corporate network after remote access is treated flat. There is a risk that users who should not have authority can access important information within the company, and information leakage to the outside may occur. This is where SDP plays a role. Regarding the first issue, SDP always maintains outbound traffic, so there is no need to keep a port open like with a VPN. When a device accesses the corporate network, the communication is relayed to the corporate system using the SDP. For the second issue, as mentioned earlier, the risk is evaluated based on the user’s attributes associated with ID and information on the connection status of both ends. Then authentication is performed, which prevents users who should not have access from accessing important information assets.
Zero-Trust Model
ZT Model Overview
So far, we have explained technologies that are deeply involved in zero trust models. Now we will consider the overall configuration of a zero trust model. The configuration can vary depending on the organization, but considered to be something like figure 5. Various resources which security is guaranteed by CSPM, CWPP, CASB, etc. are accessed from devices whose security is guaranteed by EDR or UEM. Regarding access, only users who are authenticated/authorized in IDaaS (Identity as a Service) may connect to the resource. This information is organically linked, and by blocking access from devices that are detected as dangerous in EDR and UEM, or access to cloud services that are determined to be at risk, it is possible to maintain security as a whole.
Figure 5 Zero Trust Model Overview
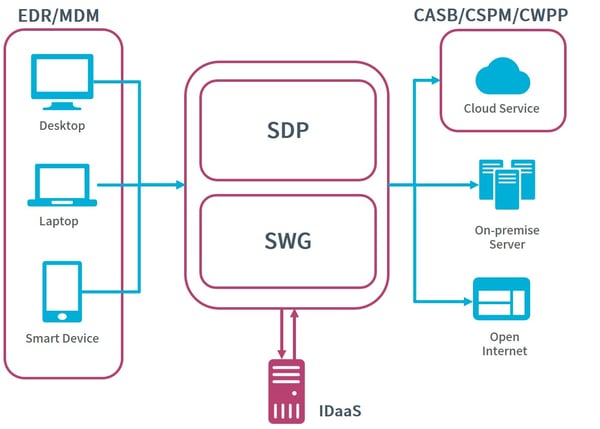
As the use of cloud services and promotion of remote work progresses, the reality of accessing the organization’s network from outside boundaries is increasing, such as accessing cloud services from an employee’s device. In these cases, a perimeter model often cannot deal with the various security risks. For example, incidents like malware infection of the user’s device due to the inability to monitor the remote device, use of online storage that is not allowed by the organization, and leakage of confidential information due to misconfiguration may occur.
On the other hand, if zero trust is adopted, these risks can be reduced. In a zero trust model, EDR can monitor endpoints and quickly restrict their connection to the network in case of malware infection. In addition, CASB, CASB, and CWPP can ensure the security of connected resources, restrict connections of services that are not allowed, and check the status of cloud service security settings. By centrally managing these access and device information by ID, it is possible to protect the entire organization from new threats.
Remote Work in Perimeter and ZT Models
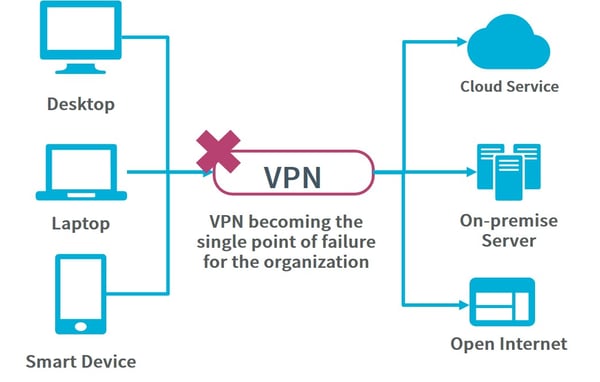
When compared to traditional perimeter models, what is the difference, especially in terms of remote work? For example, consider access to SaaS from a device. When accessing SaaS in a perimeter model, it would be connected to the internal network with a VPN and then access the service via proxy. As shown in figure 6, the overhead increases by entering the network first. And there is a concern that VPN will become a single point of failure for the organization when the number of users working from home increases.
Accessing SaaS via the internet does not go through a proxy and bypasses the conventional security measures, which leaves endpoints at risk such as accessing shadow IT (unauthorized SaaS), or accessing unauthorized sites, etc. On the other hand, in a zero trust model, the endpoint is kept safe with EDR and UEM. Access outside the organization via SWG makes it possible to access various resources while maintaining the same level of security as when inside the organization, with less overhead, even in a remote environment.
Figure 6 Challenge in Perimeter Model
Paradigm of ZT Model
In fact, Google has implemented a zero trust model called BeyondCorp, where “Context-Aware Access” is realized and determines access availability based on conditions such as connection location, device and device status based on ID, and if the security level is secured no matter where it is accessed from. It is ideal in a remote work environment to completely remove the boundaries of the organization so that the necessary information can be accessed from the necessary place by the necessary person.
Conclusion
With the Covid-19 pandemic, remote work has spread rapidly among companies and organizations. New threats and issues have become apparent as the company shifts to work styles that are different from traditional ones. As an approach that can solve those threats and issues, this paper provides an overview of technological elements that support zero trust models and the overall picture when combining them.
There are few companies like Google that are working on the realization of a zero trust model company-wide, but it is expected that the number of companies introducing it will increase in the near-future. Though new issues and threats may emerge as zero trust models becomes widespread worldwide, we would like to keep an eye on the ever-advancing zero trust model landscape.










