
Triggered by the spread of Covid-19, digital transformation (DX) has been accelerating. Regardless of the size of company, the introduction of remote work aimed at improving operational efficiency has progressed as part of "defensive DX". On the other hand, security risks targeting remote work environments are also increasing*1. Among them, “damage caused by ransomware”, which was ranked first in the IPA “Major Security Threats 2022”*2, has drawn particular attention.
*1 Digital Transformation Survey 2020 by Dentsu
*2 10 Major Security Threats 2021, 10 Major Security Threats 2020 by IPA (Information-Technology Promotion Agency, Japan)
Overview of Ransomware Attack Methods and Damage
Ransomware is a coined word between “Ransom” + “Software”. It is a type of virus that has four goals: encrypting files to make them impossible to access, hinder business operations, make it difficult to recover from the attack, and extort money in exchange for decryption. Not only can the files on the host be targeted, but also HDDs and USB memory devices connected to the device, or backups over the network.
There are ransomware that have the ability to further infect others which are accessible from the victim device, and there is a possibility that it can spread to the entire network. The main infection routes consists of email attachments and suspicious URLs for user terminals, or unauthorized external access for servers. There are also cases of infection from external storage media and terminals deployed within the same network.
In Japan, the damage is reported almost every month and there are cases in which not only terminals are infected, but also file servers and core systems. This causes confusion in business operations, interrupting control PCs in factory production lines, and forcing a suspension of continuity. The number of cases regarding infection spreading by targeting small-to-medium-sized business involved with supply chains of large companies have been increasing as well.
In the early days of ransomware from 2015, the mainstream concept was a “disruption type” that infected devices via emails sent out to an unspecified number of people. It spread by exploiting vulnerabilities in Windows OS, such as “WannaCry”, which was prevailed from 2017 and 2018.
Since 2019, “targeted attacks” aimed at servers of specific large companies and organizations that have become mainstream, ransomware instances have risen. Furthermore, the “double extortion type” that threatens to disclose stolen data, potential system destruction, and filesystem encryption has become an elevated threat since 2020.
Figure 1: Features of new types of ransomware attacks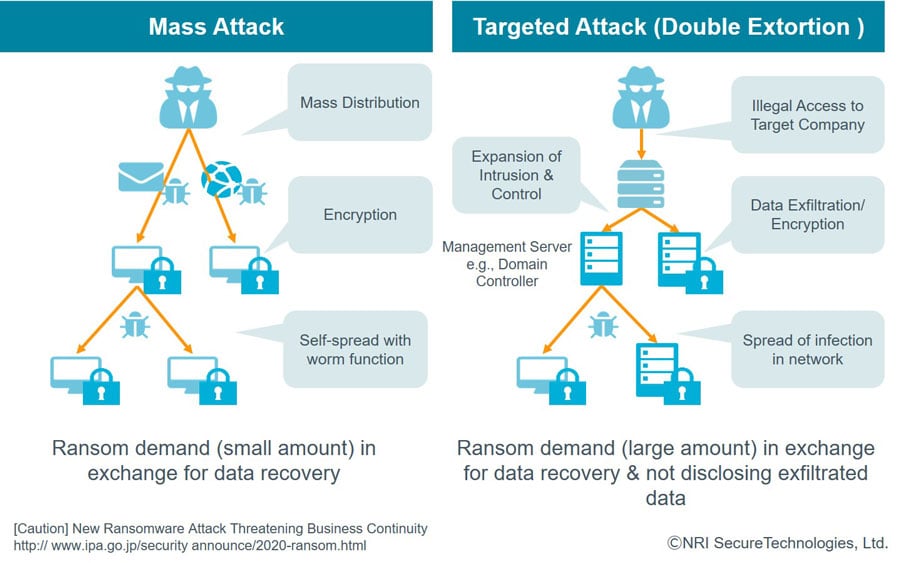
Changes in the corporate environment is the basis of ransomware’s rampage. In remote work environments, there have been rapid increases in the number of cases of intrusion. This is due to exploiting vulnerabilities in remote access VPN devices and public servers, or from the misconfiguration of public/authentication settings for remote desktop service (RDP) that were hastily installed in response to the pandemic.
Changes on the attacking side environment are also related to ransomware epidemics. An infrastructure for buying and selling “information on VPN devices and administrator accounts owned by victim companies”, “ransomware attack tools”, and “stolen personal information” has been developed on the internet. Cybercrime has been industrialized. Additionally, an environment has been developed in which crypto assets, such as Bitcoin, can be used to make payments easily and anonymously, allowing business models for attackers to be established.
Now ransomware has become one of the most watched threats by companies of all sizes, changing attack methods and targets.
1-1. Incident Cases
In November 2020, a game maker announced that its email system and file servers had been infected with ransomware due to unauthorized access from outsiders. It caused significant impact and disrupted operations. The company’s subsidiary in North America was intruded from a vulnerability exploited in an old VPN device and the infection spread via the company’s group network.
As a condition for suspending data disclosure and decryption, a ransom of 11 million dollars (1.15 billion yen at the exchange rate at that time) in Bitcoin was made, but the company refused to pay. As a result, more than 130 GB of information was disclosed, payment was demanded again, and the stock price fell sharply along with the prolonged response.
Effective Approaches to Ransomware
As attacks diversify and become more serious, there is a call for stronger countermeasures. However, since the budget and resources are limited, efficient measures are important.
First of all, it starts with knowing the environment to be protected; understand the business form, network configuration of the company, and identify use cases (who accesses business data from which device, what route, what service is used to access it, what kind of processing is performed, and where it is stored). Organize the status of security measures currently implemented in the organization as to [1] organization and policies, [2] accessing hosts, [3] work environment, [4] internet gateway, [5] internal systems accessed, and [6] cloud services. It enables to clarify necessary measures to implement, and which area needs to be improved.
Figure 2: Areas where security measures need to be implemented in organization
(Framework for organizing the current situation)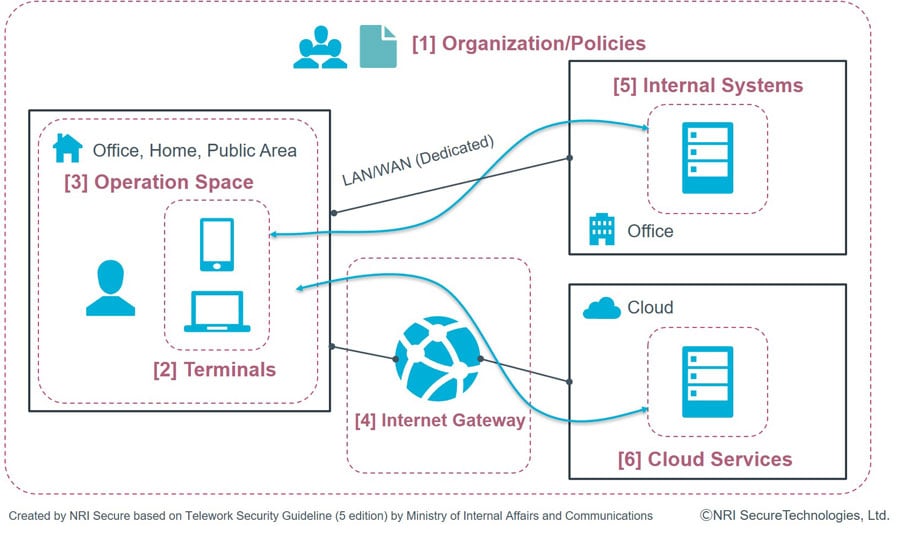
Next are the three steps of ransomware attacks (see Figure 3), classifying effective measures (best practice) for each step from the perspective*3 of “prevention”, “detection”, and “response/recovery”. After implementing basic measures such as disabling unnecessary services, installing anti-virus software, applying patches and updates, and backup which are recommended for any company size, a plan should be made considering the balance of “prevention”, “detection” and “response/recovery”.
Figure 3: Classification of ransomware response (Best practice)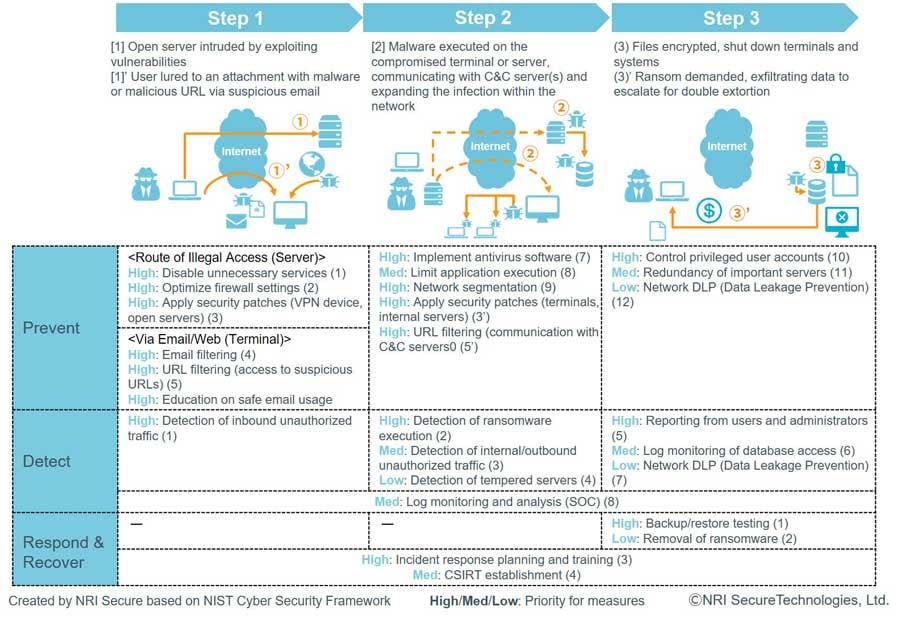
*3 Simplified view of the cyber security framework advocated by the U.S. NIST
2-1. Prevention
(1) Disabling unnecessary services
Disable services such as SMB (Server Message Block) and RDP (Remote Desktop Service) on servers in order to block intrusion routes from the outside.
(2) Optimizing firewall settings
Configure the access control list to close SMB and RDP ports to limit unnecessary access from the outside. Review it periodically.
(3) Applying security patches
Keep software up-to-date and remediate serious vulnerabilities immediately in order to prevent unauthorized access that can exploit known vulnerabilities in VPN devices and public services. It assists in limiting the spread of infection through unauthorized internal communications.
(4) Email filtering
For incoming emails, filter spam emails, dispose emails with virus or malicious URL, and authenticate the domain of email destinations.
(5) URL filtering
Block access to malicious URLs clicked in emails, as well as communication from ransomware infected devices and servers to the C&C server*4.
(6) Education on safe email usage
Confirm how to check the sender of emails and social engineering, attachments, and URLs. Periodically bring to the attention of employees’ on not opening emails if they are unfamiliar or suspicious.
(7) Implementing antivirus software
Install anti-virus software and update definition files in order to prevent virus infections of devices and servers. As a countermeasure against more sophisticated ransomware, it is recommended to monitor user behavior and block suspicious operations using EDR (Endpoint Detection and Response), especially for devices accessing the internet.
(8) Limiting application execution
Utilize the standard functions and security tools of the OS to restrict the execution of unauthorized applications. This assists in preventing the execution of ransomware and the installation of malicious software.
(9) Network segmentation
Isolate important file servers and core systems from the network segments where user terminals are deployed in order to prevent the spread of ransomware infection.
(10) Controlling privileged user accounts
Assign general user rights for terminal users, strictly manage administrator credentials, and minimize access rights to important servers in order to prevent attackers from giving administrator rights on infected devices and servers. Require two-factor authentication for remote maintenance and operation.
(11) Redundancy of important servers
Secure business continuity with redundancy for servers important for business operations. It assists in preventing service disruption due to ransomware infection.
(12) Network DLP (Data Leakage Prevention)
Block communications and outgoing emails containing large amounts of data in order to prevent important information from being leaked from file servers and databases by ransomware.
*4 Command & Control Server: A server used by attackers to maintain communications with compromised systems within a target network
2-2. Detection
(1) Detection of inbound unauthorized traffic
Detect and send an alert for any unauthorized inbound traffic at the internet gateway.
(2) Detection of ransomware execution
Detect and send an alert for any ransomware execution by anti-virus and application control on the device and the server.
(3) Detection of internal/outbound unauthorized traffic
Detect and send an alert for malicious traffic, such as outbound traffic to C&C servers managed by attackers, and lateral movement from the device infected with ransomware in the same/adjacent segment.
(4) Detection of tempered servers
Detect and send an alert for unauthorized configuration changes of servers due to ransomware infection.
(5) Reporting from users and administrators
Report to the CSIRT*5 via help desk if an event indicating ransomware infection*6 is confirmed by the user or server maintenance/operation staff.
(6) Log monitoring of database access
Detect and send an alert for unauthorized operations on critical databases due to ransomware infection.
(7) Network DLP (Data Leakage Prevention)
Detect and send an alert for outbound traffic sending confidential information at the network DLP (Data Leak Prevention) level.
(8) Log monitoring and analysis (SOC)
Build a system to monitor and analyze detected alerts and security logs, and to report suspicious incidents to a security management department such as CSIRT.
*5 Computer Security Incident Response Team: A capability set up for the purpose of assisting in responding to computer security-related incidents
*6 Symptoms such as screen lock, ransom message display, file encryption, login failures or business disruption with legitimate credentials
2-3. Response & Recovery
(1) Backup/Restore testing
Regularly backup the system/data, implement revision control and perform a recovery test at least once a year in preparation for encrypted servers. In addition, isolate any infected devices in a separate network segment to avoid spread in the network.
(2) Removal of ransomware
When OS reinstall is not an option, but removal of ransomware is required for recovery, prepare for response in advance. Assistance from a security expert is needed since ordinary antivirus software cannot clean up all traces made by the ransomware.
(3) Incident response planning and training
Organize response procedures and escalation criteria in case an incident occurs, also conduct drills once a year. In particular, ransomware often accompanies system shutdown and recovery, so it is desirable to organize business and system recovery procedures in conjunction with a BCP (Business Continuity Plan).
(4) CSIRT establishment
Build a dedicated team (CSIRT) to direct responses to alerts and reports. Be prepared to request specialized investigations (forensics) to identify causes and impact as soon as necessary.










